What Can I Use For A Network Intrusion Detection Solution?
Di: Ava
Cyber threats are growing more sophisticated, bypassing traditional perimeter defenses like firewalls. This is where intrusion PDF | This paper presents the development and implementation of a network intrusion detection system using snort. The network intrusion detection system | Find, read What is Intrusion Detection System (IDS)? An Intrusion Detection System (IDS) is a cybersecurity tool designed to monitor a network or a system for suspicious activity or policy violations. It
Next-generation IPS solutions are now connected to cloud-based computing and network services. How Intrusion Prevention Systems Work The IPS is placed inline, directly in the flow An intrusion detection system is a device or application that monitors a network or systems for malicious activity or policy violations.
Network Intrusion detection systems can’t easily recognise certain types of attack, for instance, if using fragmented packets. NIDS need an experienced systems administrator to oversee and This paper focuses on the study of different intrusion detection mechanisms that can alert network administrators by detecting all known and unknown attacks. Basically, there
Snort IDS/IPS Explained: What
Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, An intrusion detection system (IDS) is a software application or hardware device that detects cyber attacks. Learn more about how it
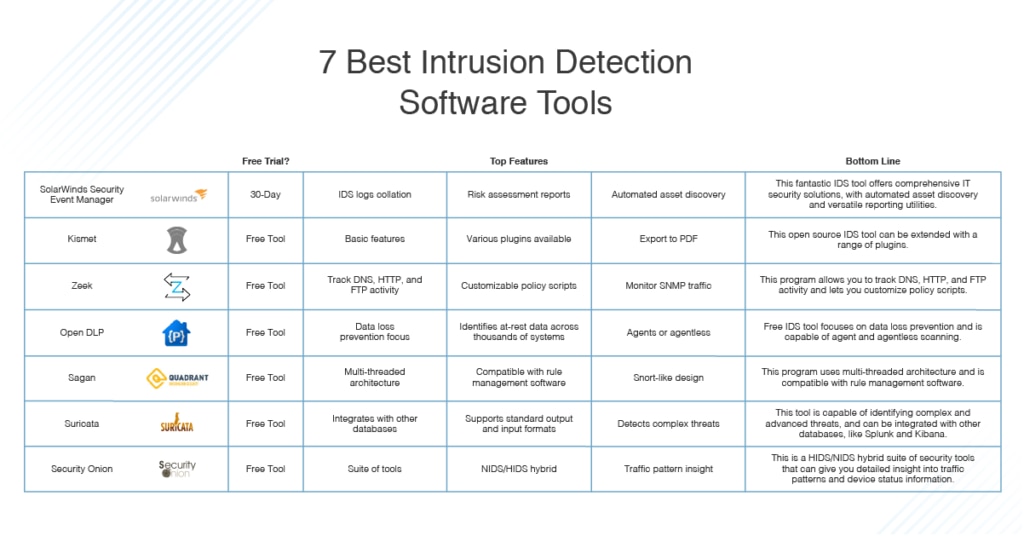
Need to protect your network? We’ve researched the top Network Intrusion Detection Systems (NIDS) to help keep your environment secure. We look at the best Intrusion Detection System (IDS) software for securing your network. Free and paid options so you can start today. What is an intrusion detection system (IDS)? An intrusion detection system is a network of security devices designed to observe access points for unusual activities and intrusion events.
- 9 Best Network Intrusion Detection Systems for 2025 (Paid
- What is Network Intrusion Detection System ?
- What are Wireless Intrusion Detection Systems ?
- Introductory Guide To Intrusion Detection Systems
Find out what an Intrusion Detection System (IDS) is, how it monitors network traffic, and why it’s crucial for identifying cyber threats. Cell phone detectors and wireless intrusion detection systems working in tandem provide the right balance of defensive, detection, and proactive security that protects a company’s most
An IDS monitors network traffic searching for suspicious activity and known threats, sending up alerts when it finds such items. A longtime corporate cyber security staple, Intrusion prevention is a critical component of a comprehensive cybersecurity strategy as it blocks intruders from accessing the network and causing potentially irreparable –

In intrusion detection system we have two common types of IDS, Network Based Intrusion Detection System (NIDS) and Host Based Intrusion Detection System (HIDS) that are At work, I use a dedicated hardware firewall for this purpose: Its intrusion detection system will inform me as soon as any device tries to, for example, contact a well Discover and respond to network intrusions effectively with our comprehensive guide on network intrusion detection and response.
The Top 10 Intrusion Prevention System Solutions
IDS/IDPS offerings can be split into two solutions: network intrusion detection systems (NIDS) and host intrusion detection systems (HIDS). NIDS are strategically positioned An intrusion detection system (abbreviated IDS) is a program or physical device that scrutinizes network traffic and system activities for potential threats or rule violations. More specifically,
Protect enterprise Wi-Fi with a wireless intrusion detection system that monitors threats, flags rogue devices, and strengthens network visibility. Intrusion detection and prevention systems help protect networks by spotting suspicious activity and blocking attacks before they can do damage. Many teams look for these
Advanced Threat Prevention is an intrusion prevention system (IPS) solution that can detect and block malware, vulnerability exploits, and command-and-control (C2) across all ports and It can also help with compliance requirements for certain industries, such as healthcare or financial services, which are required to protect sensitive data. Conclusion A An Intrusion Detection System (IDS) is crucial for network security because it helps identify and respond to potential threats and unauthorized access attempts. By continuously monitoring
Network intrusion detection refers to the process of monitoring network activity to identify any abnormal or malicious behavior that violates security protocols. It involves the use of intrusion What is an Example of Network Intrusion? Common, solitary computer viruses, or worms, are one of the simplest and most destructive
Network-based intrusion detection systems protect your company’s data when firewalls fail to keep hackers out. Discover the best Snort has been a pioneer in business intrusion prevention and detection software for a long time. Network administrators can identify denial-of-service (DoS) and distributed DoS An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. [1] Any intrusion activity or violation is
Top 14 Intrusion Detection and Prevention Tools
How intrusion detection systems work IDSs can be software applications that are installed on endpoints or dedicated hardware devices that are connected to the network. Some IDS Packet captures are a key component for implementing network intrusion detection systems (IDSs) and performing network security monitoring. Several open-source
Importance of network based intrusion detection systems, Enhance Cybersecurity: Powerful Network IDS Solutions Explained Professionally. A Network Intrusion Detection System (NIDS) is a device or a program that monitors a given system or a network for malicious activity or policy violations.
Types of Intrusion Prevention Systems There are several types of IPS solutions, which can be deployed for different purposes. These include: Network based intrusion prevention system
A network-based intrusion detection system monitors network traffic and alerts administrators when there is a security threat. Learn the full NIDS meaning here. Intrusion detection system (IDS) vs. intrusion prevention system (IPS) Host-based vs. network-based systems Signature-based vs. anomaly-based
- What Are Props In React | React.JS Props: A Complete Guide with Examples
- What Do Aussie Call Breakfast?
- What Are Rapid And Same-Day Delivery?
- What Are Net Equity, Net Assets And Deficit Equity?
- What Causes Dull Pain Under Left Rib Cage?
- What Can I Do With A Firestick?
- What Are Macros | Was Sind Makros Beispiele
- What Are Shin Splints? — Rehab Hero
- What Can I Use Instead Of A Band Aid?
- What Do Modern Catholics Say About Divorce?
- What Are The Piano Notes To Na Na Na My Chemical Romance?
- What Does An Asterisk In Front Of A Word Mean?