What Are Security Attacks? , Cyber Security Threats and Attacks: All You Need to Know
Di: Ava
The year 2024 witnessed a surge in cyber-attacks, with incidents targeting critical infrastructure, healthcare, financial institutions, and even political campaigns. As part of this blog, we will cover the most common types of cyber attacks and the appropriate countermeasures that should be taken to prevent cyber attacks
Cyberattacks are unwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer Explore recent and major cyber attacks in India, including real case studies, industry trends, and expert prevention tips. Stay ahead with Eventus Security’s analysis of evolving cyber crime. How to prevent cyber attacks and protect against the different types of cyber security threats? Explore real-life examples of cyber attack prevention
Cyber Security Threats and Attacks: All You Need to Know
Major cyber attacks, data breaches, and ransomware incidents that made headlines in February 2025, plus new malware, vulnerabilities, reports and warnings Learn about the biggest cyber threats every financial service should be aware of in 2021 and how to successfully defend against them.
MITRE ATT&CK ® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. With the creation of ATT&CK, MITRE Unpack the many and varied types of cybersecurity threats organizations face today—and the threat actors behind them.
Find latest cybersecurity news from every corner of the globe at Reuters.com, your online source for breaking international news coverage. The Hacker News is the top cybersecurity news platform, delivering real-time updates, threat intelligence, data breach reports, expert analysis, and actionable insights for infosec professionals and decision-makers.
There are various classification of security attack is as follows ? Cryptanalytic attacks These attacks are combination of statistical and algebraic techniques objective at make sure the secret key of a cipher. These technique inspect the numerical properties of the cryptographic algorithms and aims at discovering distinguishers of the output distribution of cryptographic algorithms Complete information on different types of cybersecurity threats, threat actors and best practices to protect you from cyber attacks.
Certain IoT security concerns, like botnets, are hard to forget, but others might not come to mind as easily, including DNS threats and physical device attacks.
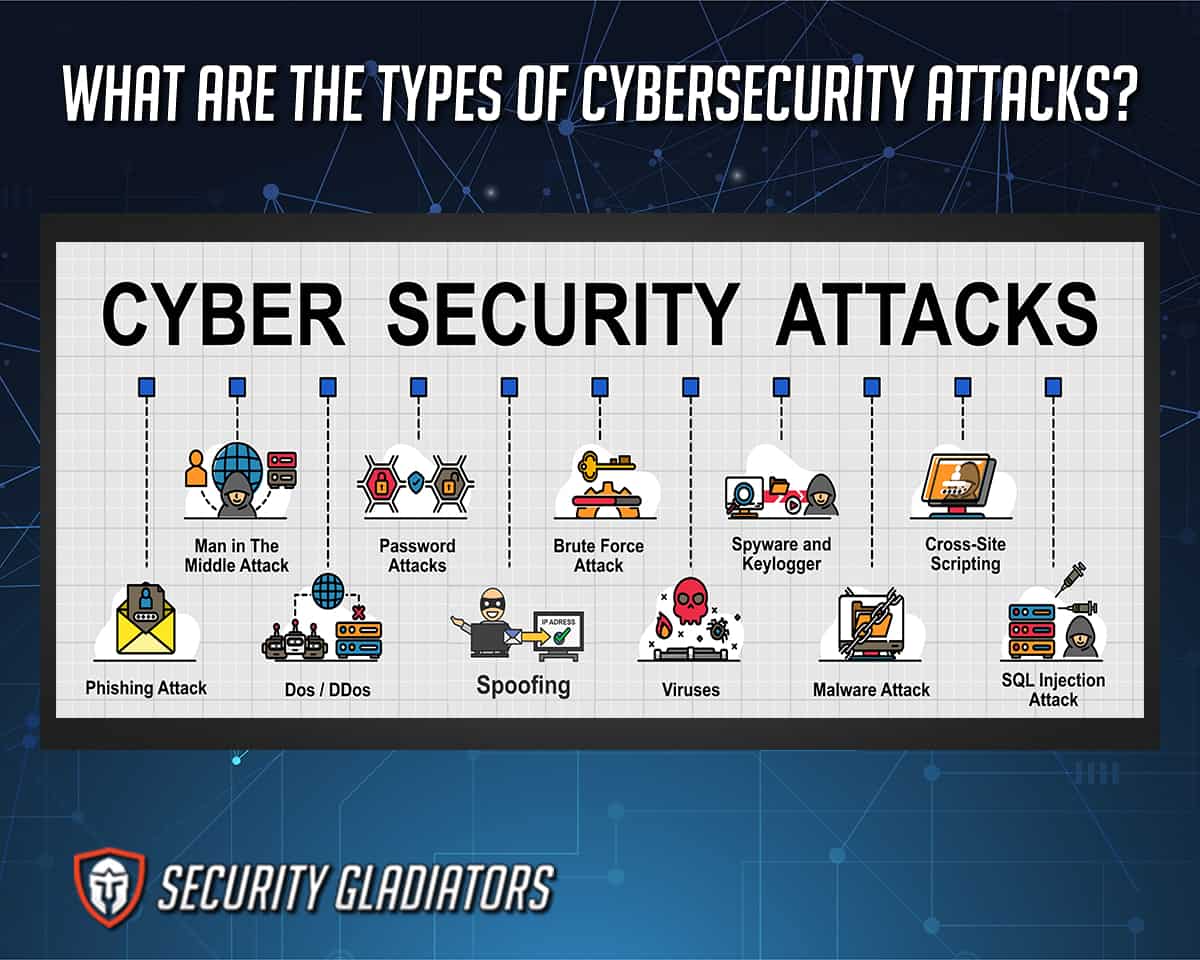
Malware, phishing, and ransomware are common forms of cyber-attacks. CISA offers the tools and services needed to protect against and rapidly respond to attacks. What is a cyberattack? Learn about common types of cyberattacks and the security threat they pose to your business, and find out how to prevent cybercrime. Phishing is a cyber threat that uses social engineering to trick people into providing sensitive information that could compromise an organization. Learn about the 19 different kinds of attacks.
Wireless networks are a common attack target. Read up on the main types of wireless network attacks and how to defend against them.
Explore Decade’s Critical OT Cyber Attacks: Uncover Top 10 Incidents Shaping Operations and ICS Security Since 2020.
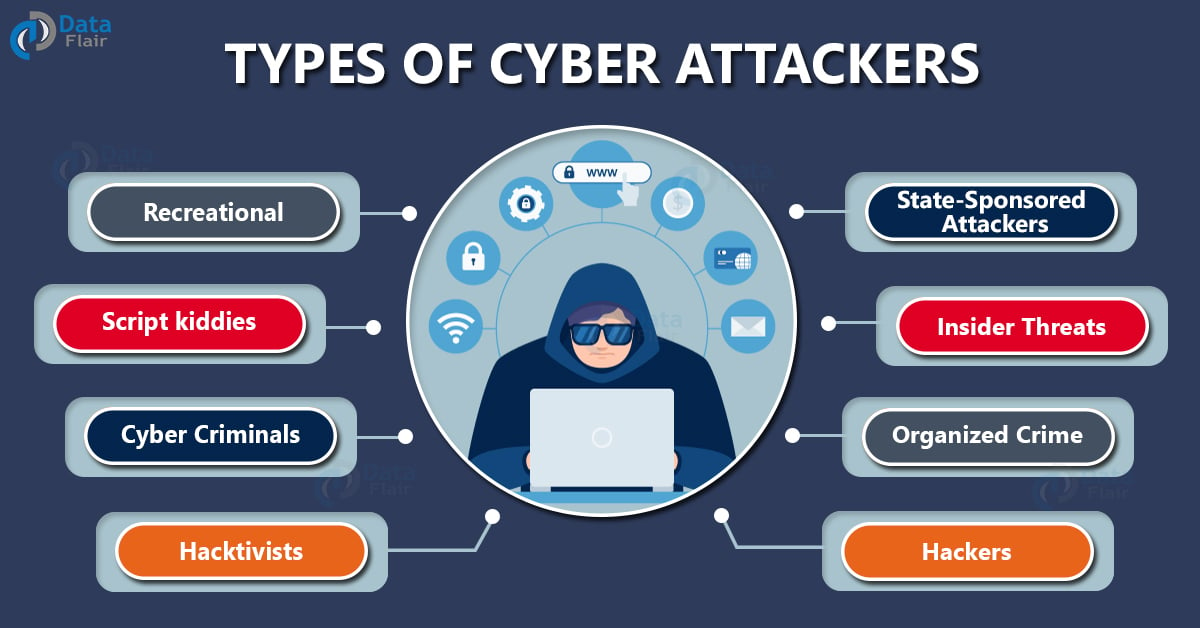
Stay updated on the latest cyber threats with our Cyber Attack Today category. We provide real-time updates on ransomware attacks, phishing campaigns, and data breaches affecting industries and individuals worldwide. Our detailed coverage includes breaking news, expert analysis, and actionable insights to help you understand ongoing cyber incidents and their implications. There are many different types of attacks in cyber security — and network security teams must worry about all of them. While no organization can protect themselves against every type of threat, a company is expected to demonstrate due diligence in protecting against the most common forms of cyber-attacks. The bulk of cyber-attacks are no longer carried out by a lone
Explore the 11 biggest hacker attacks in history highlighting breaches such as the 1999 attack on NASA or cyberattack that shut down an oil processing facility. Discover what an active attack is in cybersecurity, how it works, and the various types that threaten systems today. Learn about effective prevention strategies to protect your network and data from these direct and malicious threats.
The OSI Security Architecture is internationally recognized and provides a standardized technique for deploying security measures within an organization. It focuses on three major concepts: security attacks, security mechanisms, and security services, which are critical in protecting data and communication processes. Introduction Information security is an essential aspect of modern-day technology, and it’s vital to understand various threats that can compromise sensitive data. Two of most common types of attacks that can occur are active and passive attacks. In this article, we’ll explore differences between active and passive attacks, methods used by hackers, and ways
In what way are zombies used in security attacks? They target specific individuals to gain corporate or personal information. They probe a group of machines for open ports to learn which services are running. They are maliciously formed code segments used to replace legitimate applications. They are infected machines that carry out a DDoS attack. Explanation: This article covers 8 types of attack in cryptography and how you can protect yourself from them. Safeguard your digital assets effectively. What is a cyberattack? Learn about common types of cyberattacks and the security threat they pose to your business, and find out how to prevent cybercrime.
A security mechanism is a method or technology that protects data and systems from unauthorized access, attacks, and other threats. Security measures provide data integrity, confidentiality, and availability, thereby protecting sensitive information and maintaining trust in digital transactions. In this article, we will see types of security mechanisms. What is Network Introduction to Cybersecurity 2.1 Chapter 2 Quiz Answers – Chapter 2: Attacks, Concepts and Techniques 1. In what way are zombies used in security attacks? They probe a group of machines for open ports to learn which services are running. They target specific individuals to gain corporate or personal information. They are infected machines that carry out
Security attacks ,services and mechanisms. cryptography and network security topics covered motivation (why you (students) should learn these topics? security The attack compromised sensitive birth date, social security, and marital status information, but not medical history. The French data protection agency opened an investigation to determine if the companies complied with cybersecurity guidelines under the These attacks often bypass traditional security measures, leading to credential theft and data breaches. Meanwhile, state-sponsored cyberattacks have become more prevalent, targeting critical infrastructure such as power grids, water treatment plants, and government agencies.
Learn about cloud security attacks, top attack vectors, and best practices in 2025 to protect your cloud environment from threats. Web application attacks are malicious activities that target web applications by exploiting vulnerabilities in their design or implementation.
- Wg-Zimmer Oder 1-Zimmerappartment Gesucht In Paderborn
- Wetter Wildpark Donsbach, Dillenburg
- What Are The Best Crafting Mods For Skyrim Se
- Wetter Wettersteinstraße, Weilheim In Oberbayern
- What A Legend! Review , Finance Legend Review 2025: Is It Legit Or A Scam?
- What Are The Different Types Of Inheritance In Java?
- What Chakra Does Pisces Rule | Pisces Chakra: The Oceanic Embrace
- What Can I Use Instead Of Turps To Clean Paint Brushes?
- What Are Some Cool Last Name Ideas? Association: Celestial
- What Are Rats Afraid Of? _ Understanding Rat Behavior: What You Need to Know
- What Can I Do With A Master’S In Construction Management?
- What About Me? Meme Generator : Free AI Meme Generator: Custom AI-generated memes
- What Are The Different Types Of Balcony Grills?