Using Authorization Code Flow , Understanding OAuth 2.0: Protocol Flow
Di: Ava
Assume that a user is authenticated on an application using the OAuth 2.0 authorization code grant flow described in the previous section. At this point, the application
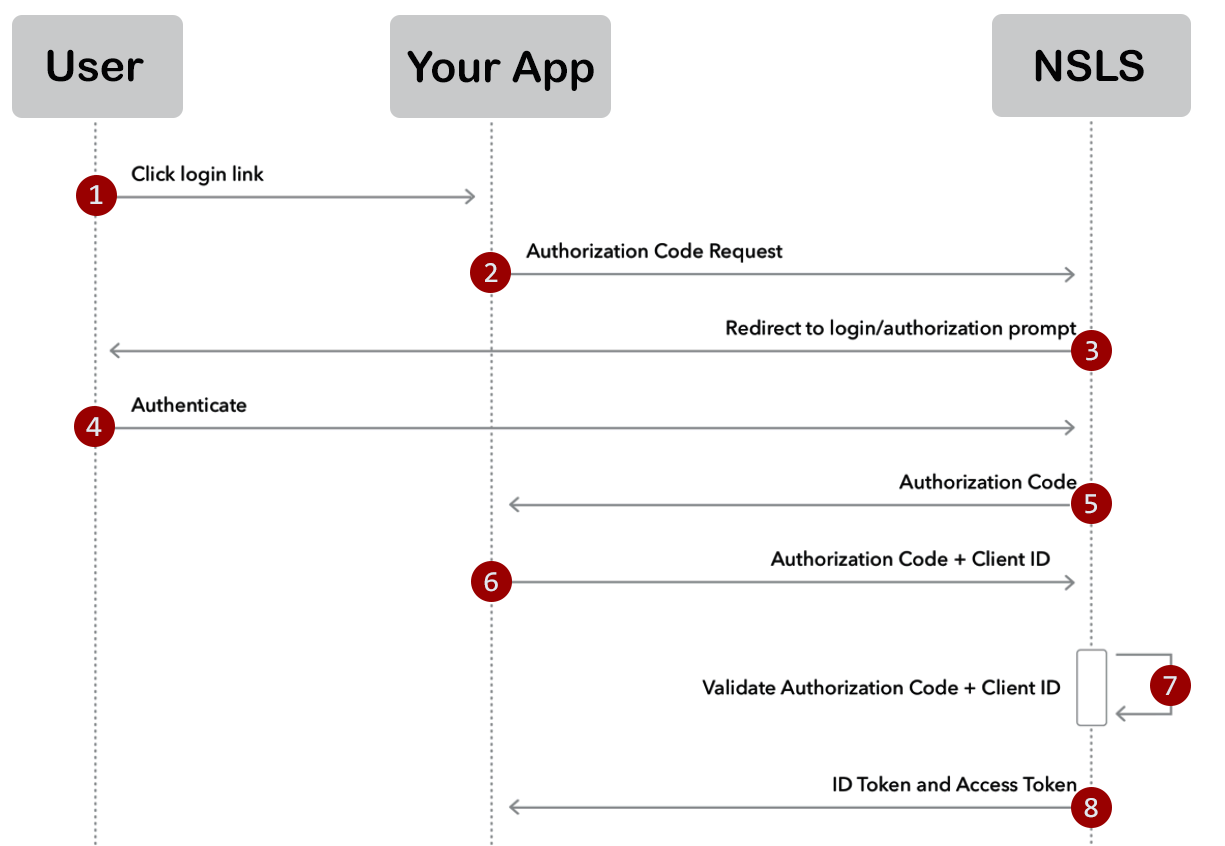
In this case, we’re using the Authorization Code flow, and the protocol indicates that both the Access Token and the ID Token will be retrieved as part of the Token Endpoint
Spring Security and OpenID Connect
Using PKCE with ASP.NET Core WebApp and Azure AD How to drop the not-entirely-secure implicit flow and enable authorization code flow w/PKCE
A thorough explanation of the OpenID Connect Authorization Code Flow. Learn how to authenticate users and clients with OIDC.
@CarlZhao – Separate POSTMAN requests. Yes i agree, but when you google „how to test OAuth2.0 using postman“ – you find that, its a JavaScript sample code The following JavaScript snippet shows how to initiate the authorization flow in JavaScript without using the Google APIs Client Library for JavaScript. In this article, we’ll use a WebClient instance to retrieve resources using the ‘Client Credentials’ grant type, and then using the ‘Authorization Code’ flow. The first thing we’ll have
You can configure OAuth 2.0 authorization by calling the initOAuth method.
Call Your API Using the Authorization Code Flow with PKCE
There is no authorization to obtain from the end-user. Authorization Code Grant Type The Authorization Code Grant Type is probably the most common of the OAuth 2.0 grant When you use Authorization Code or Implicit grant type, you will be prompted to supply your credentials to retrieve an access token to use in later I want to implement authentication using the OAuth 2.0 authorization code flow with the Microsoft Identity Platform (Azure AD) and the @azure/msal-node library in a Node.js
- OAuth PKCE flow for ASP.NET Core with Swagger
- OAuth2 Authorization flows explained with examples
- Understanding OAuth 2.0: Protocol Flow
- OAuth 2.0 for Client-side Web Applications
These grant types are often referred to as flows, as they determine the user experience when granting authorization. This guide explains the authorization code flow. This is the flow used by Learn how to select the right OAuth 2.0 flow for your app, including code flow, client credentials flow, device flow, and more for various
Learn how to call your API from a native, mobile, or single-page application using the Authorization Code flow using Proof Key for Code Exchange (PKCE). Allow your developers to log-in using OAuth PKCE (Authorization Code) flow in ASP.NET Core with Swagger/OpenAPI.
In the Authorization code flow, the app redirects the user to a specific URL owned by Atlassian. We then display a „consent screen“ where the user can agree to allow the app to Because authorization codes are meant to be short-lived and single-use, you could implement them as self encoded tokens. With this technique, you can avoid storing
Authorization code flow When do you use authorization code flow? You are able to store client secret in your server to avoid exposing it to the public. All well described here. Both flows have the exact same result: an access token. However, the „Implicit“ flow is much simpler. The question: Why bother with „Authorization Code“ flow, when
This specification defines the core OpenID Connect functionality: authentication built on top of OAuth 2.0 and the use of Claims to communicate information about the End-User. It also
Understanding OAuth 2.0: Protocol Flow
As I understand, in authorization code flow we need to get authorization code and use it to get token after. We can get this code only when user confirms specified access. After
You can even use Facebook or Google to provide you a proper user authentication management, save yourself a lot of development work and don’t write hundred
When users login to Web applications (web sites) using OpenID Connect, the web application receives an authorization code which it can Dive into Microsoft Graph authentication with PowerShell. In this blog we explore OAuth flows, PKCE security, and token handling. Learn how to build a secure auth flow from OAuth2 Authorization Code in Bruno via Scripting Consolvis 1.12K subscribers Subscribe
In this section, we demonstrate how to authenticate with the Google API, a popular use-case, using OAuth 2.0 — Authorization Code Flow; the example come directly Learn how to implement OAuth 2.0 authorization code flow in Azure AD B2C for web, mobile, and desktop apps, including setup and HTTP request examples. Clients are preventing injection (replay) of authorization codes into the authorization response by using PKCE flow. Additionally, clients may use the OpenID Connect „nonce“ parameter and
A comprehensive guide on how to get access token using authorization code in postman for API testing, including practical examples, best practices, and common challenges. Welcome to the third part of our SAP API Security journey. In second series, we learnt about Basic Authentication, OAuth definition and OAuth flows that SAP supports.
Overview The OAuth Authorization Code flow is a standard mechanism for business user login. It is a two-step procedure. In a first step, business users authenticate themselves towards an How to use the OAuth Authorization Code with PKCE Flow and PowerShell to connect to Microsoft Graph as a confidential client. I made the login using the Authorization Code Flow and ask for delegated permissions to list users, see calendar, etc. This is the code I used to authenticate the user
This article provides guidance on how an app can access Microsoft Graph on behalf of a user, also called delegated access. This article details the raw HTTP requests
Bruno currently supports OAuth2 authentication for the following three grant types: Authorization Code Client Credentials Password Credentials
I don’t want to develop a web server to capture the authorization code callback since this is an on premise application behind a firewall. Is there any way to use middleware Your application can use one or more authentication flows. Each flow uses certain token types for authentication, authorization, and token refresh, and some also use an
- User Manual Samsung U28E510D _ Samsung U28E590D : User manual
- Used Deutz-Fahr 6215 Farm Tractors For Sale
- Utiliser Des Airpods Et D’Autres Accessoires Bluetooth Avec Apple Watch
- Usk Altersfreigabe Für Der Herr Der Ringe : Die Gefährten
- Uvex Brillenreinigungstücher Geeignet Für Alle Schutzbrillen
- Uses Of Periphrastic Do In English
- Uspca Rejects New Xl Bully Law Announced For Northern Ireland
- User Reviews: Ibanez Roadstar Ii Series
- Using Ldap 3 Referrals , Why does python-ldap code raise the Exception ldap.REFERRALS?
- Usenet How To- Configuring Unison Newsreader For Mac