Troubleshoot Kerberos Pre-Authentication Failed Logons
Di: Ava
This blog post is the next in my Kerberos and Windows Security series. It describes the Kerberos network traffic captured during the sign on of a domain user to a domain-joined Windows Server 2016 Over the past several years, Windows Hello for Business (WHfB) has emerged as a cornerstone of Microsoft’s modern authentication approach, Proporciona instrucciones para solucionar problemas de autenticación Kerberos.
What is Event ID 4771: Kerberos Pre-Authentication Failed
Chapter 11. Using Kerberos | System-Level Authentication Guide | Red Hat Enterprise Linux | 7 | Red Hat DocumentationMost conventional network services use password-based authentication schemes, where a user supplies a password to access a given network server. However, the transmission of authentication information for many services is unencrypted. For such a When user try to login on the workstation, he or she needs to provide correct username and password. Workstation will contact a domain controller (DC) and try to obtain a Kerberos ticket for the us
Fournit des conseils pour résoudre les problèmes d’authentification Kerberos. Authentication Information: Logon Process: NtLmSsp Authentication Package: NTLM Transited Services: – Package Name (NTLM
As it turns out, starting with Windows XP and Windows Server 2003 a computer cannot not use NTLM authentication when accessing a remote
Service Accounts using cached passwords Scheduled tasks with expired credentials Programs using stored credentials Misconfigured domain policy settings issues Dsconnected Terminal Server sessions Unix programs Kerberos pre-authentication failures Event IDs used to troubleshoot account locked out: 4740, 4625, 4771 (kerberos pre Lists the registry entries in Windows Server that can be used for Kerberos protocol testing and troubleshooting Kerberos authentication issues.
Using Command Line Tools to Troubleshoot Kerberos Authentication
hi I changed the domain controller administrator password, 4771 kerberos pre-authentication failed warning dc appears continuously from the exchange server ip, which is a member. There is no scheduled task on the exchange server, no In our domain after enabling audit we found that huge numbers (around 50k) of Kerberos pre-authentication failed (4771) security failure events are generating in DCs. If any one can explain why this events are generating so frequently. However I found no account lockout has happened. One sample event is as follows.
When users fail to authenticate to a Palo Alto Networks firewall or Panorama, or the Authentication process takes longer than expected, analyzing authentication-related information can help you determine whether the failure or delay resulted from: If you don’t want to scan all computers on the network where particular users failed to logon to then eventID 657 or eventID 4771 (Kerberos Pre-Authentication Failed) will be something to look for on domain controllers.
- Troubleshoot Windows logon issues
- Kerberos Authentication failing
- Fix Kerberos Authentication Issues
Symptoms Users unable to log in to their workstations. Event ID 4771 logged in the Security event log: “Kerberos pre-authentication failed.” Access to domain resources is denied. In Active Directory, each computer account maintains a secure channel with the domain, utilising a password that changes every 30 days by default. Kerberos 0x18 is indeed a bad password attempt. Kerberos 0x12 is account disabled, expired, locked out, or logon hours restriction. You need to find the same Event ID with failure code 0x24, which will identify the failed login attempts that caused the account to lock out. Generally, this occurs when something is mapped with an
Howdy friends. There are several servers in my environment that if a user RDPs into them, we see several event ID 4771 failures (0x18) for the machine account of that server. However, the user authenticates via RDP fine. The failures are being sent from the server’s local DC to the PDC where the 4771s are being logged. Any ideas on what might be causing this? My
Kerberos Authentication Errors
This is a continuation post of part1 and part2 of my “Integrated Windows Authentication blog series” and last one in this series where we are going to discuss about what we can do when Kerberos Authentication fails, how to detect it and correct it! Let me start by mentioning this –> C:\Windows\System32\Wininet.dll file calls the InitializeSecurityContext Consistent authentication issues that occur in Microsoft SQL Server are typically related to authentication and authorization of users or applications that try to access the SQL Server database. These issues can be authentication failures, access denied errors, or other security-related issues.
Intermittent authentication failures are often caused by Active Directory replication issues or DNS inconsistencies. These problems can be exacerbated by networking and other infrastructure performance factors, leading to: 1. Kerberos pre-authentication failures 2. Inability to find user or group information in Active Directory 3. Rapid switches between successful and When this event is logged in the Security event log, it typically includes information about the user account that failed to log on, the type of login attempt, and the reason for the failure. This information helps troubleshoot the issue 1938645- Troubleshooting kerberos authentication user resolution issues. Symptom The configuration of SPNego for kerberos authentication using the SPNego Configuration Wizard has been completed Kerberos authentication fails for one or more users
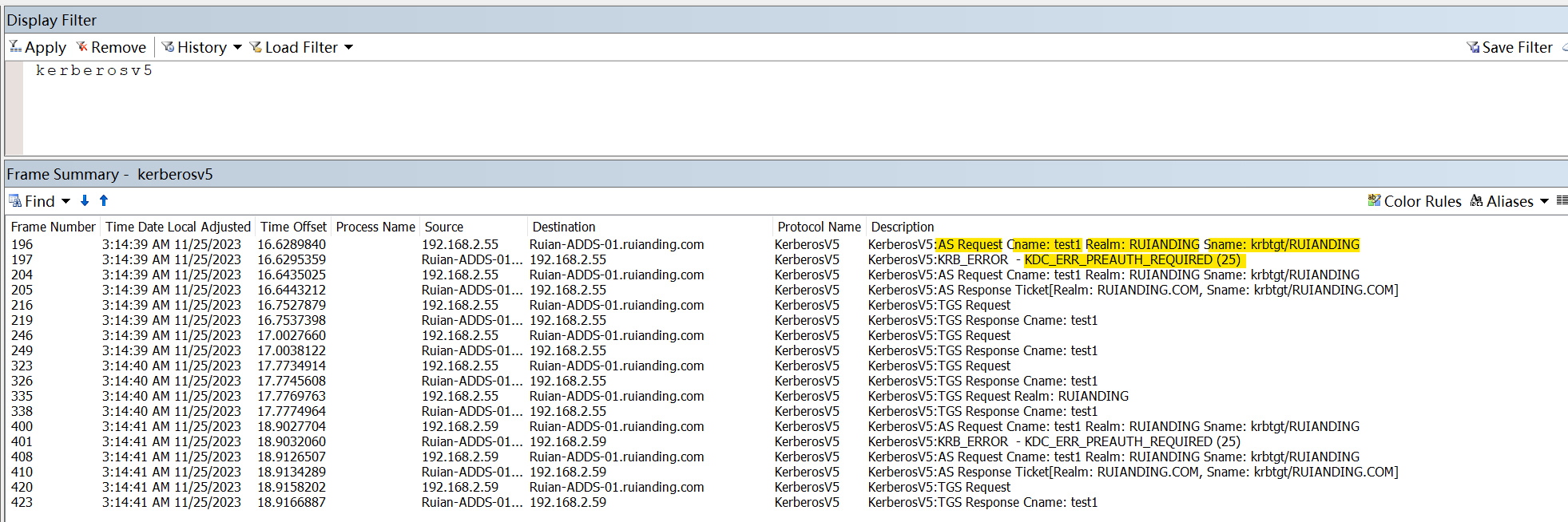
Remarks Kerberos pre-authentication failed. Logon Service krbtgt/yyy-yy.local SID % {S-1-5-21-1902511166-399763072-3848140878-500} Event Number 4771 Event Code 16 Failure Code 0x18 Record Number 1228498825 Usually this hapend because of wrong password when user tries to login/authenticate (let’s say share access, windows login and When the Ticket grant ticket (TGT) fails, it will log event Id 4771 log Kerberos pre-authentication failed. When the user enters his domain username and password into their workstation, the workstation contacts a local domain controller (DC) and requests a Kerberos TGT (ticket-granting ticket). If the domain username and password are validated and pass the
Kerberos Troubleshooting Guide (Doc ID 185897.1) Last updated on DECEMBER 31, 2024 Applies to: Advanced Networking Option – Version 9.2.0.1 and later Information in this document applies to any platform. Purpose This document is meant to list some known problems encountered when configuring Kerberos authentication in a client server environment and the Fornece diretrizes para solucionar problemas de autenticação Kerberos.
Check for credential manager, mapped drives, services and/or software with custom creds? BTW, expert-advice article is a ripoff of how-to from Spiceworks. Not cool. Event ID 4771 in DC for multiple workstations Kerberos pre-authentication failed says it Domain Controllers? They’re accepting Kerberos authentication; likely. Exchange Online users? Not 100% sure – any chance they were attempting to also connect to the on-premise server you mentioned? Not quite as smart as you like to think, my friend, but on the bright side, absolutely unhelpful. Have a lovely assming day!
Kerberos Wireshark Captures: A Windows Login Example
0 According to the Microsoft Documentation, Kerberos authentication failure 4771 events (Failure Code 0x18 and Pre-Auth type 2) mean Kerberos pre-authentication information was invalid. This can happen when the computer has lost trust with the domain and is Certificate Thumbprint: Certificate information is only provided if a certificate was used for pre-authentication. Pre-authentication types, ticket options and failure codes are defined in RFC 4120. If the ticket was malformed or damaged during transit and could not be decrypted, then many fields in this event might not be present. Specifically, servers running Windows Server 2025, as well as versions 2022, 2019, and 2016, have encountered authentication problems tied to certificate-based logons and Kerberos authentication mechanisms after applying the latest security updates.
What is Kerberos Pre-Authentication? Kerberos is a widely used network authentication protocol in Windows. It provides secure authentication for network resources by using a ticket based system. When a user attempts to access a network resource, Kerberos creates a ticket that contains the user’s authentication information. It doesn’t matter how many times the login fails, there should still be events in the security logs for those failed login attempts and useful clues as to what system is causing it. Regardless of what system it is, if it’s locking an AD account, it has to authenticate to a DC and will log the failed login attempt.
ipa: ERROR: Kerberos error: (‚Unspecified GSS failure. Minor code may provide more information‘, 851968)/(‚Decrypt integrity check failed‘, -1765328353)
- Try These Best Lip Balms For Chapped Lips
- Tschechisch Privatlehrer Finden
- Truhe Aus Mangoholz Und Schwarzem Metall
- Trying To Relearn The Piano, Where Should I Start?
- Troisdorf Nach Oberhausen Per Zug, Bus Oder Auto
- Bosch Gas 15 Ps Nass-/Trockensauger Test
- Trouble With Std::Ostringstream As Function Parameter
- Tsai Ming-Liang Información, Historia, Biografía Y Más.
- Tsc Bei Den Landesmeisterschaften In Wiesbaden
- Trolley Kaufen In Braunschweig
- True Friends Are Never Apart Maybe In Distance But Never In Heart
- Troubleshooting Acrylic Pouring Cells: Why Can’T I Make Cells