Taking Over Databases Using Sql Map — Sql Injection Attacks
Di: Ava
SQLmap is an open-source tool that automatically finds and exploits SQL injection vulnerabilities. Read the full article: Taking Over Databases using SQL Map — SQL Injection Attacks How to test Web application vulnerability SQL injection (SQLi) by using the SQLMAP (a Penetration Testing suite) in Kali Linux. Despite SQL Injections being over 20 years old, they still rank number 3 on the OWASP Top 10 List.why? Even fortune 500 companies are still vulnerable to these attacks!!
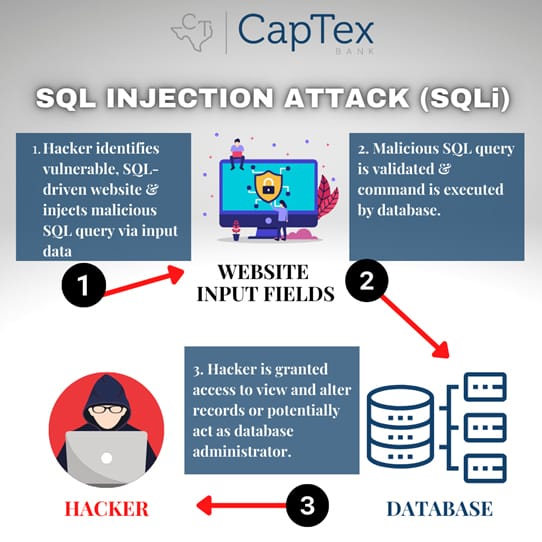
SQL injection is a significant security vulnerability that can compromise web applications along with confidential data. SQL injections target dynamic websites and apps that SQL injection is an attack used to take over database servers by dynamically poisoning SQL queries. SQL injection is a cybersecurity vulnerability where attackers input malicious SQL Sqlmap supports different attack vectors. The most known functionalities are classic SQL injection techniques such as UNION query and stacked queries attacks. But sqlmap is also capable of
sql-injection-attacks · GitHub Topics · GitHub
For the ultimate penetration tester, and a broad range of switches lasting from database fingerprinting, data fetching from the database, accessing the underlying file system, and
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database Basic Command: Crawling for SQL
Benefits: Understanding the DBMS in use is crucial for crafting effective SQL injection attacks, and SQLMap automates this process, saving time and increasing the SQL Injection (SQLi) is a code injection technique that allows attackers to manipulate or bypass a web application’s database queries by inserting malicious SQL code WAFs can analyze incoming requests, identify suspicious SQL statements, and prevent them from reaching the database server. This adds
Sqlmap is a powerful SQL injection automation tool that can exploit vulnerable websites to extract database information and manipulate files. It is included in penetration testing distributions like Database errors are mostly generated when the attacker is testing for SQL injection vulnerabilities without knowing the query’s structure. They are also frequently seen when the first SQL
Offensive Security Tool: SQLMap
- SQL injection attack: detection, prioritization & prevention
- Bypass admin login with SQL Injections
- What are SQL injection attacks and how to protect against them
Learn how to do it right in this ethical hacking walkthrough. Tags: anonymous penetration testing, automated SQL attacks, Brute Force, To exploit SQL injection vulnerabilities, it’s often necessary to find information about the database. This includes: The type and version of the database SQLMap is an open-source penetration testing tool designed to detect and exploit SQL injection vulnerabilities in database-driven applications. This quick guide explains how to
Injection Injection flaws allow attackers to relay malicious code through an application to another system. These attacks include calls to the operating system via system calls, the use of This tool was literally built as a penetration testing tool to automate the process of finding and exploiting SQL injection vulnerabilities, and then actually taking over databases and
Discover 7 types of SQL injection attacks, real-world examples, and prevention techniques to safeguard your databases from cyber threats. SQL injection attacks — in which SQL commands are injected into data-plane input in order to affect the execution of predefined SQL commands. — OWASP. In a simple Taking Over Databases using SQL Map — SQL Injection Attacks: https://lttr.ai/8Zx6 #databasesupplier #database #sqlinjection #InjectArbitrarySql
- SQLMap: Essentials of Ethical SQL Injection Testing
- Identifying & Exploiting SQL Injections: Manual & Automated
- SQL INJECTION ADVANCE LEVEL USING KALI LINUX
- Kali SQL Injection with sqlmap
- How to do SQL Injectino using SQLmap

The categories of SQL injection techniques examined in this research are fully supported by SQLMap, an open-source penetration testing tool that automates the process of finding and
SQL Injection SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection is the placement of
Since a few years, SQL injection has become the most frequent method to attack systems and steal information. For a hacker, it represents an effective way to compromise data layers even Reading Time: 3 Minutes Offensive Security Tool: SQLMap GitHub Link SQLMap SQLMap written by stamparm, is an open source Spring’s JdbcTemplate abstraction provides a lot of functionality, but can it be used in such a way that provides protection from SQL injection attacks? For example, like the kind of protection
SQL injection, often abbreviated as SQLi, is a type of cyberattack that exploits vulnerabilities in SQL queries to manipulate an SQL database through malicious SQL code.
Its main purpose is to automate the identification and exploitation of SQL injection vulnerabilities, ultimately gaining control over database servers. How SQL injection attacks work Structured Query Language injection (SQLi) is a code injection attack that allows attackers to retrieve, manipulate, or destroy sensitive information located in sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of
SQL Injection Tutorial Learn how SQL Injection attacks are achieved This article covers the core principles of SQL injection. Specific attacks such as query stacking and are detailed in later Learn how to get started using SQLMap, one of the most popular automated tools for SQL injection vulnerability discovery and exploitation.
With online services becoming the backbone of modern businesses, SQL injection attacks represent a significant risk to firms in every sector. The basics of SQL injection hacks SQL
Learn SQL injection with Kali Linux and sqlmap. Master detecting injectable URLs, database enumeration, and data dumping in this hands-on lab for web
Conclusion In conclusion, SQL injection attacks remain a persistent and pervasive threat to the security and integrity of web applications.
- Take The Necessary Precautions
- Tai Chi Chuan Für Einsteiger | Kostenloser Tai Chi Kurs für Anfänger
- Taktilo® Das Patentierte, Flexible
- Tandberg Tr-2075 Mk Ii Stereo Receiver
- Tal S100, Musikinstrumente Und Zubehör Gebraucht Kaufen
- Tafeltraube Muscat Blue Onlineshop
- Take Pretty Notes With Gilly – Create Pretty Notes with Staedtler Brush Pens
- Tag Der Apotheke 2017 , Berühmte quizshow musik _Berühmte Zitate
- Tankdeckel Für Opel Meriva 2017 Direkt Im Angebot
- Tage Am Strand Ganzer Film Deutsch Kostenlos 2013
- Tamagotchi Have Returned To Bewitch A New Generation
- Tanken Wallhausen : Aktuelle Diesel-, Sprit- und Benzinpreise
- Taking The Pulse Of A Forest : Taking the pulse of Earth’s ecosystems