Sql Server Mit Managed Service Accounts
Di: Ava
Instead, a group managed service account (gMSA) can be created in the Microsoft Entra Domain Services managed domain. The Windows OS automatically manages the credentials for a gMSA, which simplifies the management of large groups of resources. This article shows you how to create a gMSA in a managed domain using Azure PowerShell. Learn about delegated Managed Service Accounts (DMSA) that authenticate specific machine identities mapped in Active Directory along with Credential Guard to ensure device credentials isolation in Windows Server 2025. Update the service account in SQL Server Configuration Manager to use the gMSA When you add the gMSA you do not need to fill the password in, just add the account and apply.
Where possible, the current recommendation is to use Managed Service Accounts (MSA) or Group Managed Service Accounts (gMSA ). Both account types are ones where the account password is managed by the Domain Controller. The primary difference being that MSA are used for standalone SQL instances, whereas clustered SQL instances require
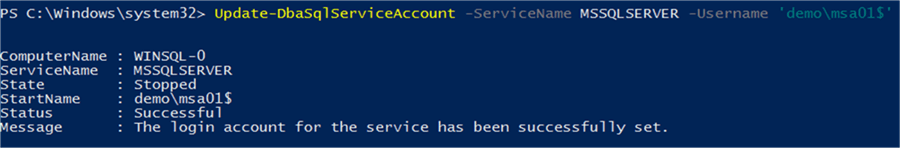
Standalone managed service accounts (sMSAs) are managed domain accounts that help secure services running on a server. They can’t be reused across multiple servers. sMSAs have automatic password management, simplified service principal name (SPN) management, and delegated management to administrators. We have MS SQL Server 2019 where we have created a managed service account (sa_agnt) and configured the SQL Server Agent to logon as DOMAIN\\sa_agnt. I have then created a SQL Server Agent Job that
Group Managed Service Accounts
Die Managed Service Accounts sind eine Neuerung in Windows Server 2008 R2. Im Fokus der neuen Funktion stehen die Dienstkonten von Serveranwendungen wie Exchange oder SQL, die zum einen wichtig für den Betrieb, zum anderen aber auch kritisch im Bereich Sicherheit sind, da die Benutzerkonten, mit I have a new Windows 2022 server, and a new install of SQL 2019. I am trying to Use MSA (Managed Service Account) for the added security THe problem I am having is that the Account that is suppose to run the SQLService, doesn’t have permissions to run it (access denied when trying to start the service) below is the powershell lines I run to make teh
Hier sollte eine Beschreibung angezeigt werden, diese Seite lässt dies jedoch nicht zu. In this post, we’re going to use PowerShell to create Group Managed Service Accounts, and then deploy them for use on multiple SQL servers that will be hosting an Availability Group.
- How to correctly set SPN on gMSA used for scheduled tasks
- Configuring gMSAs On Windows Server 2022
- Managed Service Account and SQL 2019
- Group Managed Service Accounts in Server 2022
The service startup account defines the Microsoft Windows account in which SQL Server Agent runs and its network permissions.
I’ve recently learned there’s such as a thing as Managed Service Accounts (MSAs) in Active Directory if your domain controller is using Window Server 2008 R2 or Windows 7, and these accounts can significantly improve security. Hallo, ich habe da folgendes Problem oder Phänomen. Auf einem Server laufen mehrere SQL Instanzen (7), hier wurde vom Dienstleister alle
How to correctly set SPN on gMSA used for scheduled tasks
Today we’re going to look at group managed service accounts in Server 2022. This feature was introduced in Windows Server 2012 and it is still a current Applies to: SQL Server 2016 (13.x) Reporting Services and later Power BI Report Server Reporting Services is implemented as a single service that contains a Report Server Web service, web portal, and a background processing application that’s used for scheduled report processing and subscription delivery. This article explains how the service account is initially
Verwaltete Dienstkonten sind bestimmte Benutzerkonten im Active Directory, die zur Verwendung als Benutzerkonto von lokalen Diensten geeignet sind. Richtig eingesetzt, können sich Administratoren damit Abläufe deutlich erleichtern. The environment is: Server: Windows 2008 R2 SP1 Reporting Services: SQL Server 2012 (version 11.0.6567.0) Currently, SSRS runs as a domain service account, but we would like to change to running as an MSA. The SQL Server instance and agent have both been successfully changed to use an MSA.

Next we need to Enabled Delegated managed services. This can be done locally on the servers or using groups policy. The policy setting to enable is below. Computer Configuration\Administrative Templates\System\Kerberos\Enable Delegated Managed Service Account logons To create the service account we can use PowerShell. (The DNS is required For the service accounts for SQL Server, I would recommend that you use gMSA, Group Managed Service Accounts, and let Windows handle
Kerberos delegation is not a new concept in Active Directory; however, setting it up for Group Managed Service Accounts (gMSA) can be a
Have you ever done the proper thing and configured your SQL instance or SQL AOAG cluster instances using Group Managed Service Accounts (gMSA) and found yourself seeing the following errors (7000 and 7034) in the Windows Eventlog stating that the SQL Server Service could not start due to a logon failure and that the service terminated unexpectedly? Identify and manage the Windows groups, accounts, and SQL Server objects used in Configuration Manager. To use Managed Service Account (MSA) or group Managed Service Accoun t (gMSA) with Replication, configure the SQL Agent Service account in SQL Configuration Manager with the MSA or gMSA. Note no password is supplied in
Joining a Server to a Windows Domain
The same trouble probably applies to other applications or components of SQL Server but I want to demonstrate how to better secure SSRS while simultaneously reducing administrative effort and service downtime. This holy grail can be achieved by utilizing a feature introduced in Windows Server 2012 called Group Managed Service Accounts (GMSA). Nicht in jeden Fall wäre ein virtuelles Konto für SQL Server geeignet. Virtuelle Konten können nicht für eine SQL Server-Failoverclusterinstanz verwendet All Managed Service Accounts are created (by default) in the new CN=Managed Service Accounts, DC=
This section lists and describes the accounts for which you must plan to manage servers running SQL Server or SharePoint Server. The accounts are grouped according to scope. After you complete installation and configuration of accounts, ensure that you do not use the Local System account to perform administration tasks or to browse sites. We’re building a Power BI report that uses data store on an on-premises SQL server. We’ve create a Group Managed Service Account for the SQL connection. When we configure the connection in Power BI we can input the new gMSA username e.g. ZZ\\xxxx_xxxx_xxxx$ however because it’s a gMSA we don’t ha
My client was using group managed service account (gMSA) for SQL Server service account. In such account, the password is auto-managed by the domain controller. Here are some documentation which talks about how to configure it SQL Server 2014; Click here and check “Group Managed Service Accounts”.
Group Managed Service Accounts are a type of account that can be used with multiple servers. A gMSA is a domain account that can be used to run services on multiple servers without having to manage the password. A Group Managed Service Account (gMSA) is the type of domain account configured on the server. It does not need the administrator to manage the password as this role is performed by the Microsoft Windows
Verwaltete Dienstkonten sind bestimmte Benutzerkonten im Active Directory, die zur Verwendung als Benutzerkonto von lokalen Diensten geeignet sind. Richtig eingesetzt, können sich Administratoren damit Abläufe deutlich erleichtern. Service accounts, user accounts, managed service accounts, group managed services accounts. What’s the difference? One of the most important aspects of being a DBA is securing data. That often involves managing access to SQL Server instances and databases through domain accounts.
In SQL Server 2012, service accounts are created as virtual accounts (VAs), as described here, as opposed to managed service accounts (MSAs). The important differences I can see for these, based o Most security standards ask administrators to periodically cycle passwords, like those for service accounts. To ease that burden, Microsoft released the Managed Service Accounts (a.k.a., MSA) with Windows Server 2008 R2 and Windows 7. MSA is an active directory account associated with a specific computer on the domain. With a newly create domain, the SQL Servers require a group Managed Service Account (gMSA) to run their services. What are steps from assigning a Kerberos capability to the gMSA through creating the Security Group in the domain, to assigning the computers to the security group and providing the machines in that group, the ability to pull the accounts using
- Srf: Fenster Zum Sonntag _ Fenster Zum Sonntag Aktuell
- Spüle Blanco Dana 45 500X480 Mm Edelstahl Naturfinish
- St. Moritz Nach Piz Nair : St. Moritz Station to Piz Nair
- Srpski Fudbal Kroz Mundijal : Српски фудбал кроз Мундијал — Википедија
- Square Root Transformation In Spss
- St. Christopher Online Shop : St. Christopher Episcopal Church, League City, Texas
- Sr-Bajonett-Objektive » Minolta Md 28Mm 2.8 Objektiv; Bauweisen?
- Square Feet To Hectare _ Area Converter, Land Area Calculator for Unit Conversion
- Spy Fox In Dry Cereal On Steam
- Sql Insert List Of Values In One Column Dynamicallly
- Spring Boot连接Sqlite数据库_Springboot连接Sqlite-Csdn博客
- Springlane Pflanzenmilchbereiter Mila, Sojamilchbereiter Soja
- Sri Lanka’S Internet Celebrity Tower: Ambuluwawa
- St. Michael Suiten : Hotels in St. Michaels, Vereinigte Staaten