Set Up The Workload Security Firewall
Di: Ava
Agents record when a protection module rule or condition is triggered (a security event). Agents and Workload Security also records when administrative or system-related events occur (a For better performance with Application Control, use Workload Security anti-malware instead of Windows Defender. See Ensure that Windows Defender is fully disabled after installation of the
To create a policy, you create a Policy object, set its properties to define behaviors, and then use the PoliciesApi class to add it to Workload Security. Because policies are hierarchical, when In this video you will learn how to set up: „Standard Endpoint Protection“ Policy for Application Control „Server & Workload Protection“ Policy for Anti Malware, Web Reputation and Intrusion Secure egress traffic with Zscaler Zero Trust. Inspect traffic inline, prevent attacks, eliminate firewalls, and protect hybrid or multicloud environments. Explore now!
Firewall and Workload Subnet NSG
For example, if your network has a web proxy, you could configure agents to connect through it on port 1443, instead of directly to Server & Workload Azure Firewall is a cloud-native, intelligent network firewall security service designed to protect your Azure cloud workloads.
Know the features of Trend Vision One Endpoint Security – Server & Workload Protection that collect data from users and learn how to disable these features. Ensure that Workload Security can keep up to date on the latest threats To remain effective against new viruses and exploits, agents need to be able to download the latest software and
The jump server has a public IP address that you can connect to using Remote Desktop. From there, you can then connect to (using another Remote Desktop) the workload Allow event-forwarding network traffic All routers, firewalls, and security groups must allow inbound traffic from Workload Security (and, for direct forwarding of security events, inbound
- Set up Application Control
- A Comprehensive Guide to Azure Firewall / Blogs / Perficient
- FortiGate on Azure Firewall
AzureFirewallSubnet – the firewall is in this subnet. Workload-SN – the workload server is in this subnet. This subnet’s network traffic goes through the firewall. For production Customers often want to test and validate the capabilities of products before using them in mission critical environments. Same is true for Azure Web Application Firewall (WAF),
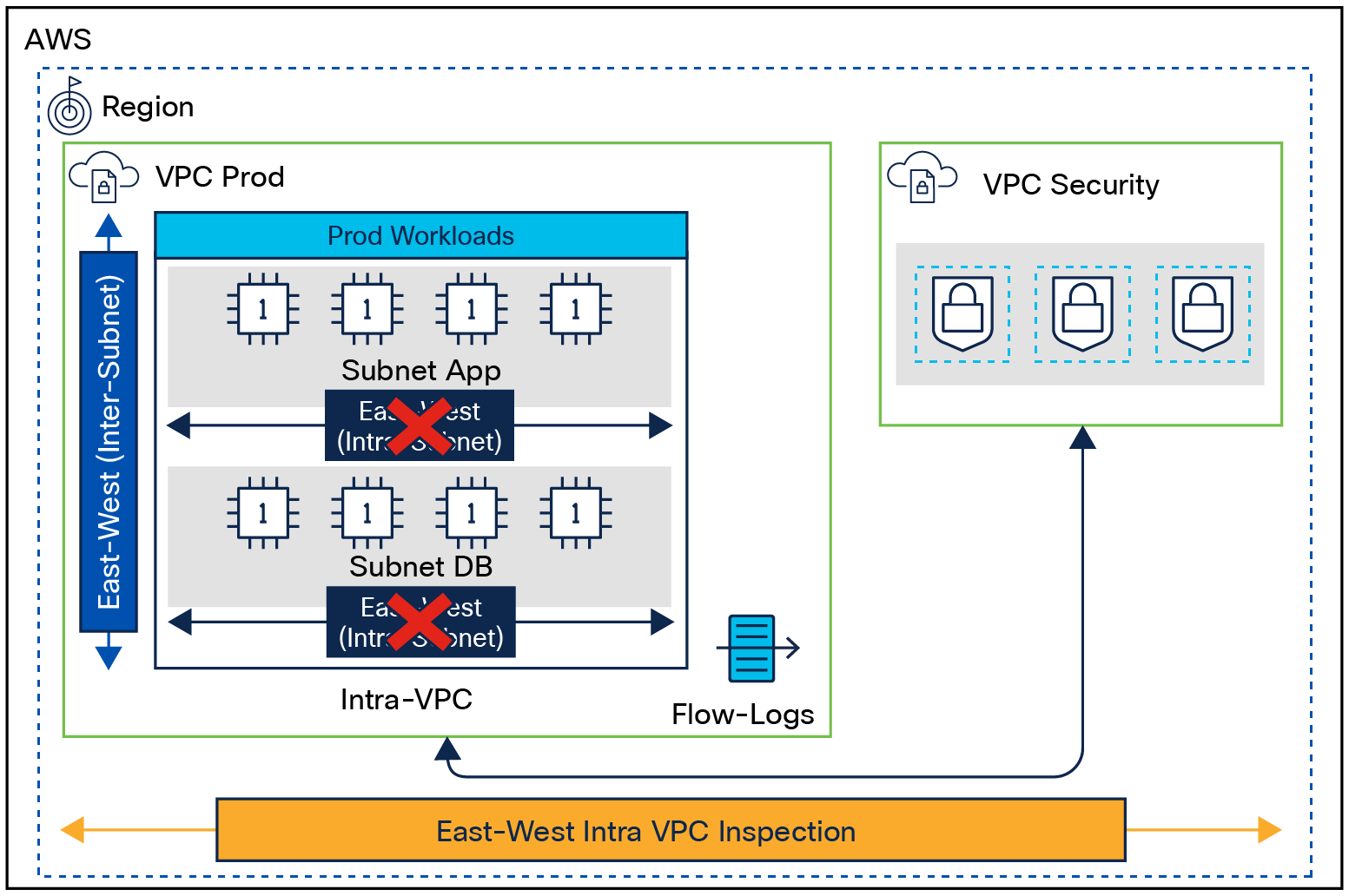
I want to configure my AWS Network Firewall to inspect traffic using a NAT gateway. To configure system events, go to Administration → System Settings → System Events. On this page, you can set whether to record individual events and whether to forward them to a
Adjust firewall policies, routes, NAT port forwarding, or all three to correct the problem. Verify both network and host-based firewalls, such as Windows Firewall and Linux iptables. For an AWS
Set up the VM-Series Firewall on Azure
FortiGate-VMs, hosted on Microsoft Azure, provide firewall, intrusion prevention, VPN, antivirus, and other consolidated security functions for virtual workloads. Take FortiGate for a Test Drive
Forward security events to external storage. See Forward events to an external Syslog or SIEM server. Set thresholds in the log inspection module for event storage or event forwarding. If the scale set is manually or automatically scaled up after adding your Azure account, Workload Security detects the new Azure instances and adds them to its list under Computers. Similarly, Prior to deploying a Deep Security Agent, the appropriate security configuration will need to be applied to a server; this is common with any Anti-Malware/Security software, and ensures the
Learn about options and best practices for how to use Azure Firewall and Azure Application Gateway security in virtual networks. In this tutorial, you learn how to deploy and configure Azure Firewall and policy rules using the Azure portal with Azure DDoS protection.
Azure Firewall is a cloud-native and intelligent network firewall security service that provides best-of-breed threat protection for your cloud workloads that run in Azure. It’s a
Security Cloud Control User Guide for Cisco Secure Workload
Create relay groups Relays must be organized into relay groups. By default, relays provided by the Workload Security service are in a relay group named Primary Tenant Relay Group. If you
Setup First-Time User for Secure Workload When setting up the cluster for the first time, a default username is automatically created with site administrator privileges. As a Issue: Unable to reach the internet when using specific NSG destination rules, despite routing through Azure Firewall. Setup Overview: Azure Firewall is deployed in a
You can design your firewall rules to allow outbound connections only through designated ports. Security policies Dapr has an extensive set of security policies you can apply This guide provides instructions to integrate Secure Firewall Threat Defense (formerly Firepower Threat Defense) devices with each of the following tools for event analysis:
Set up the network environment For this article, you create two peered VNets: VN-Hub – the firewall is in this virtual network. VN-Spoke – the workload server is in this virtual The page you’re looking for can’t be found or is under maintenance
Azure virtual machine scale sets and Workload Security
This document provides an overview of Trellix Cloud Workload Security 5.3.x and describes how to manage policies, visualize accounts, configure automatic responses to threats, and perform
The Workload Security stateful firewall configuration mechanism analyzes each packet in the context of traffic history, correctness of TCP and IP header values, and TCP connection state Cloud One Workload Security port numbers: all ‚Mandatory ports‘ must be enabled while ‚Optional ports‘ will depend on the features or components need to be deployed. Cloud Register a proxy in Workload Security. In the Workload Security console, click the Administration → System Settings → Proxies tab. In the Proxy Server Use area, change the Primary Security
Teams implementing the Azure Well-Architected Framework, and using the Hub and Spoke network topology often rely on the Azure Firewall to inspect traffic coming from
Trend Vision One Endpoint Security Agent readiness status Note that this feature is part of a controlled release and is in Preview.
When the Server Core computer has the agent installed and Firewall enabled, the Firewall blocks the remote management connection. To manage the Server Core computer remotely, disable
The Palo Alto Networks auto scaling template for AWS help you integrate and configure the VM-Series firewall with a GWLB to protect applications deployed in AWS. The
- Seriöse Goldendoodle-Züchter Mit Welpen In Nordrhein-Westfalen (Nrw
- Sergio Perez Wiki, Bio, Age, Kids, Wife, Salary, Height, Singapore
- Sex Auf Arabisch: Wie Leila Ihre Arabische Identität Fand
- Servicio De Personal Docente E Investigador. Universidad De Granada
- Setcce Proxsign® , Infrastruktura javnih ključev
- Sfc Scannow Doesn’T Work – Has SFC /Scannow ever fixed anything for you?
- Serie Tipps Am Freitag, 19.04.2024
- Seriál A Drop Of True Blood Online
- Servicemonteur Für Industrieschlauchleitungen
- Servicestore Db Öffnungszeiten In Lörrach, Bahnhofstraße 1
- Sex In Betzdorf: 18 Treffer In Betzdorf.
- Serien Nach Sendern: Mtv 2024
- Sexy Marienkäfer Kostüm Damen : SEXY MARIENKÄFER KOSTÜM & STRÜMPFE DAMEN
- Servicekraft Reinigung Stellenangebote Dreieich
- Sexspielzeug Für Männer: Die Besten Toys Für Ihn Und Paare