Sans Top 20 Critical Security Controls, Sans Security Essentials
Di: Ava
The document outlines 20 critical security controls that are viewed as effective in blocking known high-priority attacks and those expected in the near future. Fifteen of the controls can be monitored automatically and continuously. The controls focus on addressing common, damaging attacks and prioritize technical security measures that can be applied across organizations.
The SANS ICS Five Critical Controls continue gaining traction among the community as well-regarded and must-needed security controls to achieve an organization’s baseline ICS/OT Cybersecurity level.
Cyber Security Training, Degrees & Resources
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 fThe Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise was compliant, meaning they passed their Payment Card Industry (PCI) audit yet customer data was still compromised. Simply being compliant is not enough to mitigate With the changing tech landscape, v8 of CIS critical security controls presents a more consolidated approach that replaced CIS Top 20 released a while ago. This topic explores CIS 20 vs CIS 18 controls and what each of the controls is and why are these required. The newer release is known under various names such as CIS top 20 v8, CSC v8, CIS 8 controls. Smaller organizations and utilities can easily feel overwhelmed and under-resourced when facing cybersecurity threats. In a 2022 white paper, SANS Institute outlined five cybersecurity controls that together can create an efficient industrial control system (ICS) or operational technology (OT) security program—providing an effective starting point for
THE CRITICAL SECURITY CONTROLS Defend Your Organization from Cyber-Thieves: Don’t Be The Next Target Critical Security Controls – SANS InstituteTurn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
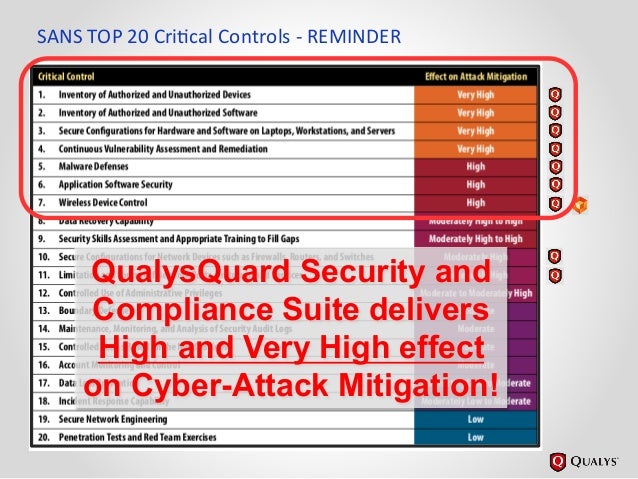
SANS Top 20 Critical Security Controls The SANS Institute recommends that every company strive to reach the SANS top 20 Critical Security Controls, these controls detail a minimum security strategy to build your organization’s cyber defense into a robust security infrastructure that combats most modern threats in order to retain the integrity of your cyber assets. I originally wrote this as a How-To, but Spiceworks’ How-To article interface was way to limited. So instead, you get it as a series of discussion Industrial Control Systems (ICS) and Operational Technology (OT) are increasingly targeted by cyber threats, putting businesses, governments, and
The complete list of CIS Critical Security Controls, version 6.1 The CIS CSC is a set of 20 controls (sometimes called the SANS Top 20) designed to help organizations safeguard their systems and data from known attack vectors. It can also be an effective guide for companies that do yet not have a coherent security program.
The ongoing evolution of the CIS Critical Security Controls
- 20 Critical Security Controls
- The ongoing evolution of the CIS Critical Security Controls
- Die 5 wichtigsten CIS-Controls, die Sie zuerst implementieren sollten
- Cyber Security Training, Degrees & Resources
SANS Institute is the most trusted resource for cybersecurity training, certifications and research. Offering more than 60 courses across all practice areas, SANS trains over 40,000 cybersecurity professionals annually. This consensus document of 20 Critical Controls aims to begin the process of establishing a prioritized baseline of information security measures and controls that can be applied across federal and commercial environments.
Discover more about the SANS ICS 5 Critical Controls for OT Cybersecurity in the third blog post of a new fundamentals series from Dragos and SANS ICS. Hundreds of organizations from national cybersecurity agencies to medium-sized companies have adopted the Critical Controls as their standard of due care, and some are reporting benefits beyond improved security. 2 With so many organizations asking for the same controls, buyers report that more vendors are competing aggressively by offering
The CIS Controls, formerly the CIS Top 20, make a strong foundation for a newly maturing cybersecurity program. Below, we explore the top 20 Critical Security Controls and their requirements. In response to the changing technology, work, and threat landscape, The Center for Internet Security (CIS) has launched CIS Top 18 Controls (v8).
CIS Critical Security Controls: A Refresher The CIS Critical Security Controls (previously known as the SANS Top 20 security controls), developed by the Center for Internet Security, provide a catalog of prioritized guidelines and steps for resilient cyber defense and information security mitigation approaches. In this article, we will delve into the SANS Top 20, a comprehensive list of the most critical security vulnerabilitiesthat organizations face today. By understanding these vulnerabilities and taking proactive measures to address them, you can safeguard your digital assetsand protect yourself from potential cyber threats.
Formerly the SANS Critical Security Controls (SANS Top 20) these are now officially called the CIS Critical Security Controls (CIS Controls). CIS Controls Version 8.1 includes updated alignment to evolving industry standards and frameworks, revised asset classes and CIS Safeguard descriptions, and the addition of the “Governance” security Introduction The SANS Twenty Critical Security controls is an important initiative designed to consolidate a number of the most important security standards and initiatives into one, clear set of guidelines.
- CIS Critical Security Controls List
- Performing ICS/OT Security Assessments
- CIS Critical Security Controls are essential for your security
- The Ongoing Evolution of the CIS Critical Security Controls
What are the 20 Critical Security Controls? The 20 Critical Security Controls for effective cyber defense (sometimes called the SANS Top 20) are split into three groups: Basic CIS Controls (1-6) are the starting point for any organization’s cybersecurity Foundational CIS Controls (7-16) Organizational CIS Controls (17-20) For more information about CIS critical The CIS Security Controls, formerly known as the SANS Critical Security Controls or the SANS Top 20, are a set of best practices organizations can use to strengthen their cybersecurity posture. These controls provide a simplified and prioritized approach to threat protection, compliance with industry regulations, achieving essential cyber hygiene, and
The Ongoing Evolution of the CIS Critical Security Controls
The SANS Top 20 Critical Security Controls is a prioritized set of best practices for cybersecurity, designed to help organizations improve their security posture and protect against today’s most common cyber threats. These controls are based on real-world data and expert input from security professionals, and are regularly updated to reflect the evolving threat landscape. In This paper sets forth the five most relevant critical controls for an ICS/OT cybersecurity strategy that can flex to an organization’s risk model,
Die Liste der CIS Critical Security Controls (ehemals SANS Top 20 Controls) ist der Goldstandard für die Beratung von Sicherheitsbeauftragten. Hier sind die Aufgaben, die Sie zuerst erledigen sollten.
View all White Papers or search and filter to find a specific page White Paper Listing Page The Center for Internet Security (CIS) Top 20 Critical Secu-rity Controls (previously known as the SANS Top 20 Critical Security Controls), is an industry-leading way to answer the question on every security practitioner’s mind: As a student of the Critical Security Controls two-day course, you’ll learn important skills that you can take back to your workplace and use your first day back on the job in implementing and auditing each of the following controls:
Reinforce critical cybersecurity skills to secure industrial control systems and operational technology against emerging threats while maintaining operational The Center for Internet Security (CIS) Top 20 Controls, formerly known as the SANS Top 20 Critical Security Controls, provide a prioritized set
Cloud security encompasses technologies, policies, and controls that protect data, applications, and infrastructure in cloud environments. Knowing how to safeguard sensitive information in cloud environments is crucial for preventing cyber threats, ensuring compliance, and maintaining business continuity. If you saw the recent Top 10 Malware January 2020 post by the Center for Internet Security (CIS), you may be wondering how to better protect your organization. CIS’s Top 20 Critical Security Controls (previously known as the SANS Top 20 Critical Security Controls) can help you map your current security protocols against a defined framework. We’ve assembled
SANS IT Audit Curriculum Roadmap SANS IT Audit curriculum features courses developed specifically for auditors and managers responsible for overseeing an IT audit or security team. Combining a mix of theory, hands-on and practical knowledge, SANS audit courses provide best practices and technical how-to’s to help you conduct effective, thorough IT audits. SANS TOP 20 CRITICAL SECURITY CONTROLS FOR CYBER DEFENSE In conjunction with the SANS Institute, the Center for Internet Security (CIS) created a list of Top 20 critical security controls (CSC) to protect organizations against cyber crime. The controls were created based on recent cyber attack methods, targets, and trends. 米国CIS(Center For Internet Security)のサイトにて、NRIセキュアテクノロジーズの翻訳による「CIS Controls」の翻訳版を公開しています。 長年にわたり、多くのセキュリティ基準や要件のフレームワークが、システムと重要データへのリスクに対処するために開発されてきました。しかし、それらの
PDF files/SANS Top 20_DS_DIG 2017
In order to help, the SANS Institute, working in concert with the Center for Internet Security (CIS), has created a comprehensive security framework—the Critical Security Controls (CSC) for Effective Cyber Defense (often referred to as the SANS Top 20)1—that provides organizations with a prioritized, highly focused set of actions that are “the Center for Internet They were once introduced as the SANS Critical Security Controls (SANS Top 20) in 2008 by an international, grassroots consortium bringing together companies, government agencies, institutions
- Sankt Michael Gaststätte Aus Wuerzburg Speisekarte
- Sarı Nokta Hastalığı Nedir? Tipleri
- Sasu : Avantages : SASU : Définition et avantages de ce statut
- Sat.1 Will Rtl Und Seine «Sofa Stars» Ausstechen
- Sanitär Notdienst Rheinbach – Klempner Rheinbach-Ramershoven ᑕ ᑐ Sanitär- & Heizung Notdienst
- Sanssouci Elfenbein Ramona Kaffee-Untertasse
- Santa Clause: Sendetermine Disney Channel
- Sanoma Is An Innovative And Agile Learning And Media Company
- Sanct Bernhard Camu-Camu- 120 Kapseln
- Santexpat, Assurance Santé Pour Les Expatriés
- Satellit-Projekt Startet: Internet Aus Dem All
- Sap As Java Super User – Explaining the Basic Architecture of AS ABAP and AS Java