Misconfiguration Attacks: 5 Real-Life Attacks And Lessons Learned
Di: Ava
Admir Dizdar Misconfiguration Attacks: 5 Real-Life Attacks and Lessons Learned Read more Security Testing September 27, 2021
Discover the 5 worst phishing attacks, their impact, key lessons, and expert tips to protect yourself from email scams and cyber In this article, we delve into 7 real-life attack path scenarios that our in-house experts encountered while utilizing XM Cyber’s Exposure Management Platform in customers’
Learning from Mistakes: Security Breach Case Studies
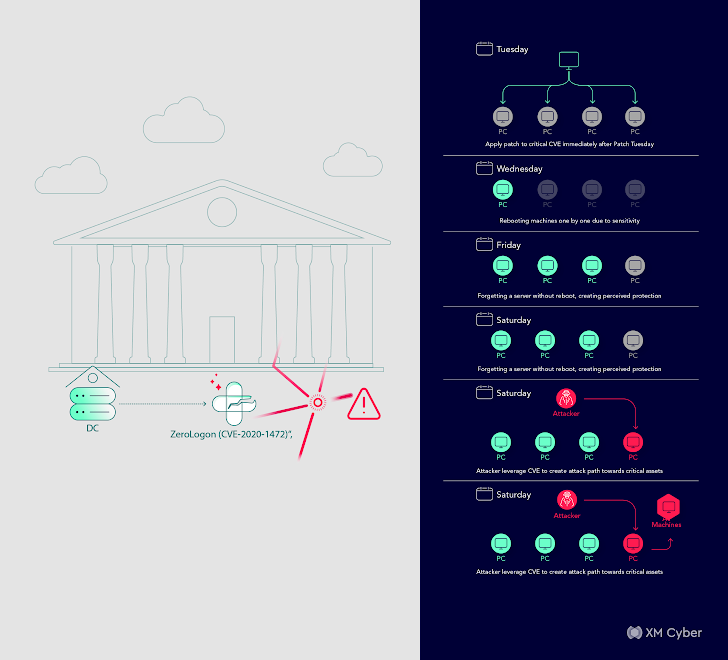
Learn everything about the Target data breach. Discover what happened, who was affected, lessons learned and more. The attack led to widespread fuel shortages and economic disruption. Key Lessons Learned: Critical Infrastructure Protection: This
In this blog, we will delve into real-world security breach case studies to understand the mistakes made and the lessons learned.
Learn about security misconfigurations, their types, impact, real-world cases, detection methods, and how SentinelOne helps prevent them. Discover the Hadrian Blog – the hub for cybersecurity insights. Learn from the experts at Hadrian, ensuring your digital world is always secure.
Misconfiguration Attacks: 5 Real-Life Attacks and Lessons Learned brightsec.com Bright 3 465 abonnés
- A Case Study of the Capital One Data Breach
- Learning from Mistakes: Security Breach Case Studies
- 18 Major Cyberattack Examples and Their Impacts
- Phishing Case Studies: Lessons Learned From Real-Life Attacks
Disclaimer To do this analysis of the Viasat cyber attack, I used the open-source intelligence (1) of the team composed by Nicolò Boschetti (Cornell University), Nathaniel Explore preventable cyber-attacks and learn key lessons to strengthen your organization’s cybersecurity defenses against future threats. This article examines actual phishing incidents, offering explanations for the strategies used by the attackers,
18 Major Cyberattack Examples and Their Impacts
This blog delves into real-life phishing incident case studies, shedding light on the tactics used, the consequences for the organizations involved, and the invaluable lessons
SaaS Attacks: Lessons from Real-Life Misconfiguration Exploits As the cloud leak and fail constantly, it's good for you to be aware of the main reason of cloud Security misconfiguration attack is what happens when the responsible party doesn’t configure its assets properly. Security misconfiguration can cause millions in damages, so read up about
Learn from real phishing disasters that rocked major organizations. Discover key phishing disaster lessons and how to protect your business with modern prevention strategies.

Leverage educational content like blogs, articles, videos, courses, reports and more, crafted by IBM experts, on emerging security and identity SaaS Attacks: Lessons from Real-Life Misconfiguration Exploits As the cloud leak and fail constantly, it's good for you to be aware of the main reason of cloud failure and leaks, A growing number of phishing attacks are making headlines today. Phishing is arguably the most common type of cyberattack, with millions of incidents recorded yearly.
Real-World Cyber Attack Case Studies and Lessons Learned In this eye-opening episode of „Mastering Cybersecurity,“ we dive into some of the most significant and impactful
Unraveling Real-Life Attack Paths
Discover the lessons learned from the latest and biggest data breaches involving insiders. Learn more about the incidents and why they happened in the first place. The data breach of Turkish Pegasus Airlines in 2022 reignited discussions around unstructured data and the nuances surrounding its security, especially in cloud environments. With the
Discover the major cyberattack examples from 2020 to 2022 and learn from real-world incidents. Understand the impacts and protect your organization.
Recovering from a ransomware attack shouldn’t be a mysterious process. A sysadmin reveals all the best guidance to get through it. Discover the most impactful cyber-attacks of 2024, including ransomware and data breaches targeting healthcare, cloud platforms, and critical infrastructure. Learn key It’s unfortunate but true: SaaS attacks continue to increase. You can’t get around it, COVID-19 accelerated the already exploding SaaS market and caused industries not
Understand the severe security risk of security misconfigurations, see common examples of misconfigurations and learn
Real-Life Phishing Cases: Insights and Lessons for Awareness
One of the greatest difficulties for understanding the modus operandi of the successful attacks that compromised billions of records in the recent years is obtaining detailed information on the
As the IoT continues to evolve and expand, the lessons learned from past XSS incidents are invaluable. By prioritizing vulnerability mitigation, adopting a security-by-design approach, Best Practices to Prevent HTTP Security Misconfiguration Attacks Preventing HTTP misconfigurations requires a proactive approach, setting secure defaults, regular We explore 10 high-profile cloud security failures, each one providing a vital lesson in the importance of robust security practices.
Important lessons are revealed by the examination of real-world situations, including the need for strong user training programs, the incorporation of AI-powered phishing detection systems, and In the second hypothesis, the misconfiguration of the WAF enabled reaching the SSRF-vulnerable application that was then used to In today’s interconnected world, the maritime industry faces a growing threat from cyber attacks, which can jeopardize not only shipping operations but also global trade and
Tactics, Techniques, and Procedures (TTPs), and learn from the attacks. We also look at examples to analyse the effect of APTs across a range of industries such as healthcare, Cyber Security & Ethical Hacking The Biggest Cyber Attacks of 2025: Lessons Learned and the Need for Cybersecurity Experts By Boston Institute of Analytics January 22, Explore preventable cyber-attacks and learn key lessons to strengthen your organization’s cybersecurity defenses against future threats.
From AI-powered deepfake scams to supply chain ransomware, explore real-world cyber incidents from 2024–2025 and what they teach us about preparing for the threats
- Mit Dem Gespür Für Menschen – gutes Gespür für Menschen
- Mit Günstigen Preisen Ist Dm Solutions Ihr Shopware Anbieter
- Mirka Exzenterschleifblatt Abranet Grip 150Mm K500, 50Er-Pack
- Mission Du Canada À Bruxelles, Union Européenne
- Mit Hund Vs. Ohne Hund _ Hunde-OP-Versicherung 2025: Die Top 10 Anbieter im Test
- Minijob It Jobs In Karlsruhe | Karriere bei der Deutschen Bahn
- Miss Germany 2024: Angehende Diakonin Kira Geiss Gewinnt
- Mir-Tauchboote: Zwillinge In Dunkler Tiefe
- Mister Spex Collection Lian 1203 003 Brille Kaufen
- Minijobs Nebenjob In Detmold – Jobs Detmold Stellenangebote, Arbeit
- Missal Católico Do Dia: Sábado, Fevereiro 3 2024
- Mistrial About To Be Declared In Eagle Poaching Case
- Mit Meinem Lieblingsthema Für Wittlin Stauffer Im Einsatz!
- Minimass 50W Attenuator , Stand alone vs. built in attentuator question