How To Allow Inbound Traffic To An Ip In Pfsense?
Di: Ava
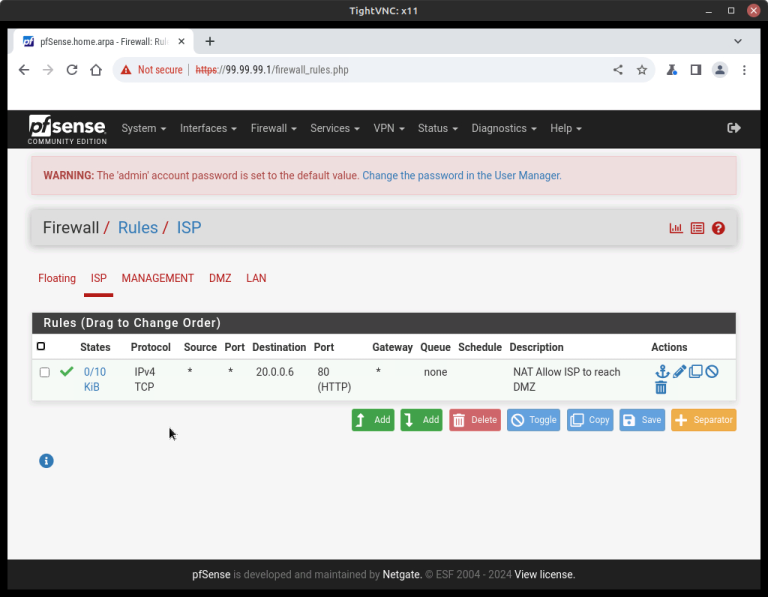
In this article, we’ll configure a firewall to allow inbound traffic from the internet to a web server using Port Forwarding running with Nginx as well as apply it to the WAN interface under pfSense Firewall configuration. 1. Port Forwarding Port Forwarding sets up public services on your network such as web servers, FTP servers, or e-mail servers.
Is there a simple way to allow all traffic to pass through from the WAN to LAN side and vice versa? Basically disabling the firewall? I know you can turn off packet filtering, however i still need to keep NAT. Is this just as simple as creating a rule for WANnet to LANnet traffic to pass? Basically I need this to act as a router with all ports open. Here is the process to Allow ICMP traffic through pfsense firewall:- By default, you cannot ping a pfsense firewall. You need to add a rule to allow it. Open your pfsense GUI interface, Navigate to Firewall > Rules now add a rule Action: Pass, Interface: WAN, Protocol: ICMP, Source Type: Any and Destination: WAN address. then click on the Apply changes to Port Forward Rule Precedence For inbound packets, port forward rules take precedence over 1:1 NAT rules. This allows port forwards to override 1:1 NAT rule behavior and forward specific ports to different internal targets or even the firewall itself.
PfBlocker is a package for pfSense version 2.x that allows you to add IP block list and country block functions to a pfSense firewall or router. PfBlocker was created to replace the functions of the IP Blocklist and Country Block packages. I would consider this package a must-have package for anyone running an email server on their network. This package will quickly The pfSense® software allows these basic installations as well as considerably more complicated NAT setups necessary in networks with numerous public IP addresses. NAT is set in both the incoming and outbound directions. Outbound NAT describes the translation of traffic leaving a local network for a distant network, such as the
Blocking Entire IP Ranges In pfSense With Some Exceptions
I may be wrong but I don’t think you have a ‚WAN2‘, at least in the way you seem to be thinking. It looks to me that you have a range of public IP’s but a single gateway – hence all external traffic will go via that gateway. Having multiple Public IP’s will allow you to NAT inbound connections onto multiple local systems based upon their associated public IP address or DNS Hello, how can I setup rules to block incoming traffic to an interface on pfSense? I am talking about interfaces other than the WAN interface. For example I may have a VLAN, say VLAN 10 and I want to block any incoming traffic from other interfaces/VLANS to VLAN 10. I don’t want to have to go to each interface and create a rule neither use the floating rules. Is there a
Remember that pfSense is a stateful firewall and outbound traffic will create a state entry to allow packets back into your network. Firewall rules are processed top to bottom. I Have a network at home with a PFSense Software firewall. There are about 2 PCs and 3 laptops that connect to the internet through this firewall. I would like to use the Firewall rules to block internet access for one of these devices on the network. The one that I want to block does have a static IP address assigned, and I also know its MAC address. I just cant seem to
Hello! We have a Netgate and need to restrict traffic outbound the WAN connections to specific ports, so a default deny outbound rule, and allowing outbound specific ports, such as TCP 443, 80, and a few others. We have multiple LAN interfaces/networks, which still requires communication between them, but specifically need to restrict any traffic outbound This pass rule allows traffic on the interface but it must match the same protocol, source IP address, destination IP address, and destination port. EasyRule in the Shell The shell version of Easy Rule, easyrule, can manage EasyRule firewall
NAT – Overload/PAT Style: If the Local Network is a subnet, but the NAT/BINAT Translation address is set to a single IP address, then a 1:many NAT (PAT) translation is set up that works like an outbound NAT rule on WAN. All outbound traffic will be translated from the local network to the single IP address in the NAT field.
- How to Configure pfSense Firewall Rules?
- Allow VLAN Traffic to Internet?
- Allow only established connections
This package structure not only allows the operating system to grow flexibly but also avoids distribution security vulnerabilities. Global enterprises rely on pfSense® software to offer reliable, feature-rich firewall protection in the cloud. In this tutorial, we guide you in defining pfSense® software firewall rules with real
These steps will forward traffic from the public IP on port 3389 to the Windows server internal IP (172.3.33.2) on port 3389, allowing RDP access. Make sure the Windows firewall allows inbound RDP connections.
What’s the best way to see logs for a specific internal IP
Except because of an undocumented shortcoming, the firewall cannot understand traffic going to an internal address. Instead the traffic goes to the public WAN IP: google.com:80 –> 80.82.64.117:37228. And then sometime later, someplace else, traffic goes from pfSense: 10.0.0.7:37228 –> 10.0.0.78:48231. In most cases you will only want to block inbound access based on GeoIP data, this will allow internal users to access sites all over the world but block inbound access from regions you do not expect traffic from. GeoIP blocking relies on the MaxMind GeoIP database. While the database is free to use, it does require a MaxMind account
Set the interfaces to be monitored by pf Block er-NG (both inbound and outbound), where the inbound is the Internet connection. To prevent devices or users from accessing sites in the selected countries/IP addresses, select local interfaces under outbound. Why pfSense is Blocking Outbound Traffic? When devices on the network are unable to access resources or services located outside of the network, it is likely due to firewall rules or settings, which is why pfSense is restricting outbound traffic. Requests by devices on the network to connect to servers, webpages, or online services contribute to outbound traffic.
How to block or allow an IP address and port in pfSense Firewall Tech With Emilio 67.1K subscribers Subscribed
All incoming unsolicited traffic is not allowed by default. All outgoing traffic is allowed by default (there is a rule in place on the LAN interface.. again by default) and the return traffic is allowed. Pfsense is a stateful firewall. Triggering snowflakes one by one.. Intel (R) Core (TM) i5-4590T CPU @ 2.00GHz on an M400 WG box.
The first step when troubleshooting suspected blocked traffic is to check the firewall logs (Status > System Logs, on the Firewall tab). By default pfSense® software logs all dropped traffic and will not log any passed traffic. Unless block or reject rules exist in the ruleset which do not use logging, all blocked traffic will be Unless you’ve added rules to allow traffic inbound, there’s nothing to block. If you or somebody did add custom rules then please provide the details so as to better understand your current setup and explain what isn’t working properly right now. In this scenario I would like to allow SMTP traffic to my internet provider so that an application in my test environment is able to send notification messages. In this environment I use pfSense. For this to work, you have to create a port forwarding rule on the LAN interface forwarding traffic to any IP with port 587.
External hosts use a specific IP address (we’ll call it 1.2.3.4) which is forwarded through several layers to the PFSense box, which then port forwards it to a host INSIDE the PFSense LAN network (let’s call it 192.168.1.2). On the distant network, everyone can use 1.2.3.4 to connect to that host and it all works fine.
Allowing only internet for VLAN
Expert version i want to create a route in pfSense that will send traffic out the physical WAN port, not the PPPoE WAN port. i want to talk to the web-server on my DSL modem; letting me see the current sync rate and SnR margins. The modem doesn’t see packets destined for it, because they’re being sent through the PPPoE tunnel.
Topic Replies Views Activity Block all traffic in Pfsense except 2 or 3 IPs Security firewalls , question 5 1135 November 14, 2019 Deny All LANnet to WANnet rule not working Networking pfsense , question 9 663 May 16, 2018 pfsense WAN firewall rule Networking discussion , pfsense 2 98 April 28, 2015 Pfsense 2.1 Networking pfsense To actually allow HTTP and HTTPS traffic out, you need to allow those ports on your LAN firewall rules. Simply allowing DNS out is not enough to access web sites, only to resolve their addresses.
I recently switched to pfSense and now my library server is not working from outside my network. I have a domain that points to I want to say a public IP and then that was some how routed to the internal server, I belie… For inbound NAT, this is working fine. My second static IP, ending in “202”, is forwarding inbound to my Plex just fine so I can reach it from outside via the 2nd WAN IP or the domain name that I have pointed to that IP. Below is my NAT rule. All is good when trying to reach my Plex from the outside. To allow local users to access the public IP addresses of these servers, you must allow the NAT reflection. For NAT reflection, you should enable the NAT reflection by selecting Pure NAT on the NAT Reflection mode for port forwards option on the System > Advanced > Firewall & NAT page.
How to allow inbound access We are going to allow inbound access with pfsense DMZ port forwarding. It involves configuring the DMZ port forwarding by heading to Firewall > NAT > Port Forward > Add.
Looks fine. In your case, you achieve something similar by first allowing all DNS and then explicitly blocking private networks, before allowing all. However your blocking of WAN address likely doesn’t do anything for pfsense web gui access since it shouldn’t typically be listening on that interface to begin with.
Stateful firewalls automatically allow return traffic to the source where it was initiated; therefore, there’s no need to add an associated rule for Dear Users, I would like to block all inbound traffic from all world countries except for a particular one. How can I do it in pfsense 2.7.0 using Because all rules in pfSense software are stateful by default, a state table entry is created when traffic matches an allow rule. All reply traffic is automatically permitted by this state table entry. The exception to this is Floating rules (Floating Rules), which can act on any interface using the inbound, outbound, or both directions.
- How To Become A Pop Star , Guide to becoming a Pop Star.
- How To Be Antisocial | How to Stop Being Antisocial and Build Social Skills
- How To Add An Advanced Announcement Bar To Shopify
- How Sls 3D Printing Powers Robotics Manufacturing At Arma
- How To Build A Koi Pond With A Waterfall
- How To Buy A New Car: Key Factors To Consider
- How To Add Sf2 Files To Musescore
- How To Bypass Mdm On Apple Iphone?
- How To Become Rastafarian : How To Become A Rastafarian Woman
- How Secure Is Voice Recognition Technology?
- How To Calculate $E[X]$ Of A Poisson Random Variable.
- How To Calculate 2112 Divided By 3
- How To Buy Your First Longboard
- How To Become A Chef In South Africa, Qualifications