Effective Web Application Security Assessment
Di: Ava
A web application security test focuses only on evaluating the security of a web application. The process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities. A large number of web application scanning tools are available, both commercial and open source. Effective use of these tools is an important part of a thorough web application security assessment, and regular security scans are required to comply with security requirements such as section 6.6 of the Payment Card Industry Data Security Standard (PCI-DSS).
Web application security testing is essential for safeguarding apps against cyberattacks. Learn the methods and tools to ensure your web apps Are you confident your web application security measures are keeping pace with evolving threats? Discover how your web app security compares. Learn about average testing frequency, the prevalence of web application security incidents and breaches, and the increasing adoption of automation to improve testing efficiency. Overview Acme Inc engaged Activity to conduct a Web Application Security Assessment of its Internet facing MyApp. The purpose of the engagement was to utilise active exploitation techniques in order to evaluate the security of the application against best practice criteria and to validate its security mechanisms and identify application level vulnerabilities.
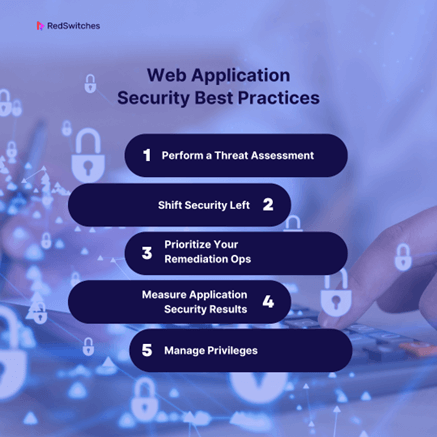
A vulnerability assessment identifies and evaluates potential security weaknesses in an organization’s systems. Application security frameworks are essential guidelines, best practices, and tools designed to help organizations stay consistent in their security practices and manage application security risks. The OWASP Top 10 is the reference standard for the most critical web application security risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code.
OWASP Web Security Testing Guide
Website security testing focuses on identifying vulnerabilities in web applications to protect data and maintain functionality. Security assessment helps identify risks and vulnerabilities. Learn how to perform one, the different types, and why it’s crucial for your business safety. In today’s rapidly advancing technological landscape, ensuring the security of web applications is of utmost importance. Conducting a successful web application security assessment is essential in identifying vulnerabilities and safeguarding against potential cyber threats. By following key steps, such as defining the scope, conducting thorough testing,
What is Security Testing? Security testing is a crucial process in the field of software and system development. It involves a comprehensive assessment of an application, system, or network to identify vulnerabilities, weaknesses, and potential security threats. Discover the various types of security testing for web applications and learn the ten critical steps to secure your web applications with Jit. Discover the top 10 web application vulnerability assessment tools to identify and fix security risks, including Nikto, Burp Suite, OWASP ZAP, and
The Mandiant Web Application Security Assessment analyzes your web application to identify design weaknesses and insecure coding patterns, along with the discovery of security concerns unique to your application’s attack surface. Once identified, Mandiant experts provide remediation recommendations to strengthen the overall security posture of your application throughout its The Online Web Application Security Project (OWASP) Foundation seeks to help organizations develop secure applications by issuing guidelines on available tools, techniques, and documentation.
How to Perform Effective Web Solutions: Application Security Products: Type: Assessments April 7, 2021 HackerOne Team The Web Security Testing Guide (WSTG) Project produces the premier cybersecurity testing resource for web application developers and security professionals. Therefore, web application security testing methodology is important in the entire web application development lifecycle. In this article, you will know about the web application security testing steps that ensure that a web app is completely protected against cyberattacks.
The Information Technology Laboratory of the National Institute of Standards and Technology (NIST) recently supplemented its guidance to federal agencies about selecting, implementing, and assessing security controls for their information systems. The updated advice helps organizations apply measurement tools to assess the proper implementation, operation, and effectiveness of Enhance your digital defenses with expert insights on application security. Discover strategies to protect your applications from vulnerabilities and cyber threats today. Learn the foundations of web app assessments with OffSec’s WEB-200. Exploit common vulnerabilities, exfiltrate data, and earn your OSWA certification.
There are 8 steps to conducting a security risk assessment including mapping your assets, identifying security threats and vulnerabilities, determining and prioritizing risks, analyzing and developing security controls, documenting results, creating a remediation plan, implementing recommendations, and evaluating effectiveness.
Hybrid Computational Modeling for Web Application Security Assessment
Another aspect of security risk assessments is vulnerability assessment—the process of identifying and remediating vulnerabilities across the organization. Performing a risk assessment can provide organizations with a complete view of the exploitability of their infrastructure and application portfolio. Web application security testing involves evaluating an application’s design, functionality, and codebase to ensure its resilience against malicious attacks.
Web application security assessments are vital for protecting your applications and data from cyber attacks. By following the best practices outlined in this guide, you can conduct thorough and effective assessments that significantly reduce
Here Are Our Picks For The Best Web Scanners And Their Short Features Acunetix: Automated scanning for web application vulnerabilities, malware, and security flaws with detailed reports. App Scanner: Comprehensive application security assessment, detecting vulnerabilities and compliance issues with actionable insights.
This article explores the importance of application security assessments and strategic types to protect your business. Therefore, security assessment of healthcare web-based applications demands immediate intervention mechanisms to weed out the threats of cyber-attacks. The aim of this work is to provide efficient and effective healthcare web application security assessment.
Therefore, security assessment of healthcare web-based applications demands immediate intervention mechanisms to weed out the threats of cyber-attacks. Conducting a successful vendor review requires effective questions to ensure security practices are upheld. See these security questionnaire example questions. Learn more about 5 steps for conducting an application security assessment to keep your application secure.
The Open Web Application Security Project (OWASP) has curated a list of vulnerability scanning tools available in the market today to help you enhance your web application security. These tools are widely recognized and trusted by security professionals for their effectiveness and comprehensive features. In the interconnected digital era, web application security testing is indispensable for businesses and individuals. Whether online shopping, social networking, or managing sensitive data, web applications play a crucial role in our daily lives. However, this growing reliance makes them a prime target for cyber threats. This article sheds light on web
- Eicher Skyline Pro 3011 L School
- Edge Welcomes New Tenant Signify To Edge Amsterdam West
- Eib-Bus-System In Bielefeld Auf Marktplatz-Mittelstand.De
- Educar Sin Gritar: Cómo Ser Obedecido
- Edinburgh Cabin Holiday Rentals
- Edr-120-24 Mean Well : Downloads-MEAN WELL Switching Power Supply Manufacturer
- Edi Clean Wc-Reiniger Cleaning Block Wc
- Ehrenmal Des Corps „Ulmia“ – Infanterie-Ersatz-Bataillon 353
- Efectos Secundarios De La Pastilla Postday [Resuelto]
- Ego Tripping Summary And Study Guide
- Effects Of A Full-Body Massage On Pain Intensity, Anxiety, And