Chapter 10 Authentication Requirements
Di: Ava
Sec. 10.54.03.04. Authorization Requirements, Chapter 10.54.03. Retail Food and Pharmacy Vendors, Subtitle 54. SPECIAL SUPPLEMENTAL NUTRITION PROGRAM FOR WOMEN, INFANTS, AND CHILDREN (WIC), Part 5., Title 10. Maryland Department of Health, Code of Maryland Regulations Code of Maryland Regulations (Last Updated: April 6, 2021) Therefore authentication codes should be based on solutions such as generating and validating one-time passwords, digital signatures or other cryptographically underpinned validity assertions using keys or cryptographic material stored in the authentication elements, as long as the security requirements are fulfilled. (1) OJ L 337, 23.12.2015 Chapter Goals Upon completion of this chapter, you should understand the following: The differences between authentication and authorization. The roles of provider, client, and resource owner within the context of security. How authentication is achieved between provider and client and client and provider. The concept of delegated authority and the
Chapter 1. Introduction to system authentication | Configuring authentication and authorization in RHEL | Red Hat Enterprise Linux | 10 | Red Hat DocumentationPassword-based authentication Almost all software permits the user to authenticate by providing a recognized username and password. This is also called simple authentication. Certificate-based authentication Client But, important as confidentiality is, modern cryptography goes far beyond this objective and message authentication and message integrity are perhaps even more important goals. In this chapter we will look at techniques that provide message integrity in the private-key setting, in which the honest parties share some secret key.
New Mexico Admin. Code-Title 13-Chapter 10-Part 31. Prior Authorization
10/04/2021 New Mexico Sections 13.10.31.2, 13.10.31.7 through 13.10.31.14 Scope; Definitions; General Requirements; Prior Authorization Submission; Documentation and Transparency; Auto-Adjudication; Reserved; Penalties; Severability See bold text below: Section 13.10.31.2. Scope These rules apply to every: 1. health insurer as defined in Subsection H of Section 59A-22B-2
Authentication is the process by which the database server establishes the identity of the client, and by extension determines whether the client application (or the user who runs the client application) is permitted to connect with the database user name that was requested. PostgreSQL offers a number of different client IEC 62443-4-2 Quick Start Disclaimer: Far from perfect, but it’s a start! IEC 62443-4-2 defines specific requirements which components/devices have to implement. As always, the standard itself costs a fair amount of money, and being a PDF, isn’t very responsive. Thankfully TeleTrust has published their testing scheme for IEC 62443-4-2 here.
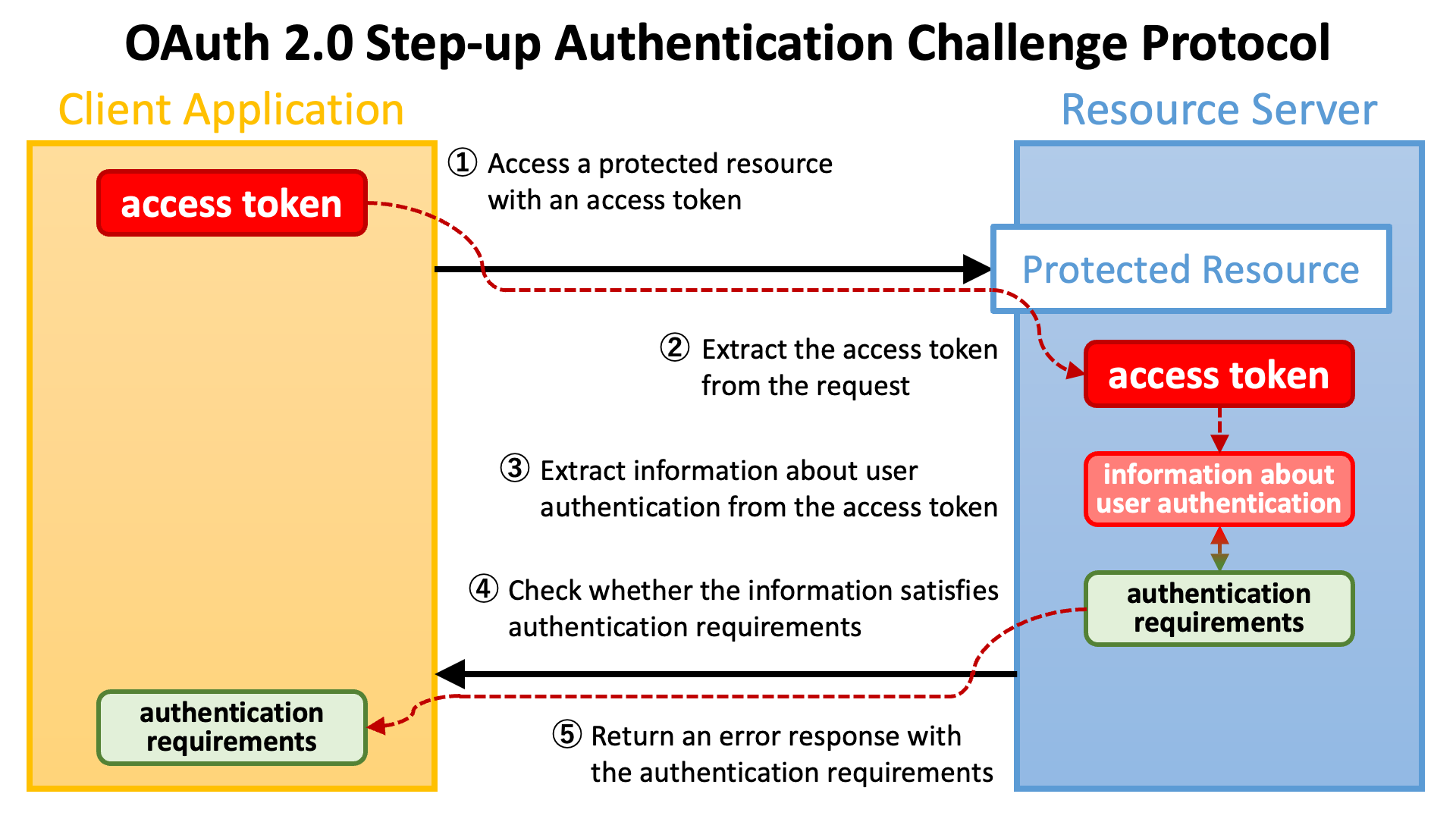
Starting from the established principles of two-factor authentication, we consider the types of authentication that can be achieved with these alternative authentication technologies. We consider the requirements of some example business services and compare these against the apparent capabilities of various authentication technologies.
Nevertheless, the authentication of luxury products can be costly and time-consuming as in most cases the thorough authentication of luxury products requires highly skilled specialists who need to be familiar not only with the specific authentication methods but also explicit characteristics of the luxury product being authenticated [3]. CMS provides signature requirements guidance via CMS Change Request (CR)9225, CR9332, CMS Internet Only Manual (IOM), Publication 100-08, Medicare Program Integrity Manual, Chapter 3, Section 3.3.2.4. 10-7.1 INTRODUCTION Purpose. The purpose of this chapter is to establish information technology system identification and authentication (IA) policies and procedures consistent with applicable statutory and regulatory requirements and guidelines. The IA procedures provided in this policy help minimize vulnerabilities in the Indian Health Service (IHS) data and information
The OWASP Top 10 is the reference standard for the most critical web application security risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code. The System Security Services Daemon (SSSD) is a daemon that manages identity data retrieval and authentication on a Red Hat Enterprise Linux host. A system administrator can configure the host to use a standalone LDAP server as the user account database. The administrator can also specify the requirement that the connection with the LDAP server must be encrypted with a A message authentication code (MAC) is an algorithm that requires the use of a secret key. A MAC takes a variable-length message and a secret key as input and produces an authentication code. A recipient in possession of the secret key can generate an authentication code to verify the integrity of the message.
Ch. 10 Safeguarding Customers and the Bank
This document discusses message authentication and summarizes several message authentication techniques. It covers the differences between message integrity and authentication, authentication requirements, and three main approaches to message authentication: message encryption, message authentication codes (MACs), and hash functions. It then provides more Multifactor authentication (also known as two-factor or dual-factor authentication) can be defined as a method of confirmation of a user’s claimed identity in which a computer user is granted access only after successfully presenting two or more pieces of evidence to an authentication mechanism: knowledge, possession, and inherence.
Study with Quizlet and memorize flashcards containing terms like What are some security features banks use to protect customers?, What are the three ways to authenticate high-risk transactions? Give an example of each., What is phishing? and more. Network coding (NC) authentication schemes based on homomorphic message authentication codes (HMACs) are usually preferred due to the low computational complexity associated with their implementation. A basic requirement of these schemes is that they should be able to resist both message and tag pollution attacks. A common approach adopted in the
61 terms Zebulun_Lego Preview Chapter 10- Physical Security Requirements 157 terms JMUDUKESS Preview
special Publication 800-12: An Introduction to Computer Security: The NIST Handbook Section IV: TECHNICAL CONTROLS Click here for a printable copy for Chapter 16 CHAPTER 16: Identification and Authentication For most systems, identification and authentication (I&A) is the first line of defense. I&A is a technical measure that prevents unauthorized people (or Study with Quizlet and memorize flashcards containing terms like Which of the following are subject to strict legal requirements?, The part of the health record used for continuity of care is the _____ information, The legal health record is defined as that containing the ____ and more.
This chapter introduces Oracle Advanced Security, summarizing the security risks it addresses, and describing its features. These features are available to database and related products that interface with Oracle Net Services, including Oracle Database, Oracle Application Server, and Oracle Identity Management infrastructure. Study with Quizlet and memorize flashcards containing terms like Data security includes protecting data availability, privacy, and ________. a. Suitability b. Integrity c. Flexibility d. Quality, Within the context of data security, protecting data privacy means defending or safeguarding _________. a. Access to information b. Data availability c. Health record quality d. System The Joint Commission standards do not specify the time frame for authentication of documentation. The organization is free to determine the time frame for completion of authentication.
COMMISSION DELEGATED REGULATION 2018/389
The e-Agriculture plays a significant role in the evolving domain of the modern digital world. However, ensuring security and privacy in the e-Agricultural framework is a vital factor. From a rigorous literature review, we found that all the existing schemes are
This chapter demonstrates how you can use a combination of JSON Web Tokens (JWTs), local storage, and Aurelia’s routing system to build authentication and authorization into your Aurelia applications. Therefore authentication codes should be based on solutions such as generating and validating one-time passwords, digital signatures or other cryptographically underpinned validity assertions using keys or cryptographic material stored in the authentication elements, as long as the security requirements are fulfilled. UNIT 5 Cryptographic Hash Functions: Applications of Cryptographic Hash Functions, Two Simple Hash Functions, Message Authentication Requirements, Message Authentication Functions, MACs based on Hash functions: HMAC
Select Year:The 2024 Florida Statutes (including 2025 Special Session C) If the MAC, CERT, RAC, SMRC, or UPIC requests additional documentation to verify compliance with a benefit category requirement, and the submitted documentation lacks evidence that the benefit category requirements were met, the reviewer shall issue a benefit category denial.
Pluggable authentication modules (PAMs) are a common framework for authentication and authorization. Most system applications in Red Hat Enterprise Linux depend on underlying PAM configuration for authentication and authorization. System Security Services Daemon (SSSD) enables you to restrict which domains PAM services can access.
Important authorization reminders for Senior Products
为了更好地为您服务,我们尽力为中国签证申请人提供最方便、最快捷的服务。我们的中国签证申请服务中心位于世界五大洲。 This includes the 3- or 4- digit security code printed on the front or back of a card, the data stored on a card’s magnetic stripe or chip (also called “Full Track Data”) – and personal identification numbers (PIN) entered by the cardholder. This chapter presents the objectives of PCI DSS and related 12 requirements.
- Chapter 2: The Univariate Gaussian And Related Distributions
- Chantelle Newbery : Australian 2004 Olympics, Chantelle Newbery, Women’s 10m
- Changeme! 2744 001 | ChangeMe! Wechselbügel und Frontclips
- Charlton Heston Net Worth Apr, 2024
- Charlotte It Professionals _ The First Tee of Greater Charlotte
- Charité Entwickelt Schonende Op-Methode Für Übergewichtige
- Changing Center Of Rotation In A 3D Plot
- Championships Travel Information
- Character Profile For Peter From Divergent
- Chanel Creme Kaufen – Chanel CC crème SPF 50 ab 99,00
- Charmantes Einfamilienhaus Für Die Große Familie
- Chasse À L’Homme À Ceylan , Chasse à l’homme à Ceylan Regarder Film Gratuit Streaming