Certverifycertificatechainpolicy Function
Di: Ava
I’m struggling to get my Windows 8 application to communicate with my test web API over SSL. It seems that HttpClient/HttpClientHandler does not provide and option to ignore It extends the function of the certification authority and enables the Application of regulations to realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft certificates One or more certificates to verify. If no certificates are given, verify will attempt to read a certificate from standard input. Certificates must be in PEM format. VERIFY OPERATION
Learn about certutil, a command-line program that displays CA configuration information, configures Certificate Services, and backs up and restores CA components in Windows. The revocation function was unable to check revocation because the revocation server was offline on application hosted on IIS Adrian Adamiak 15 Apr 12, 2023, 11:37 PM You’re viewing Apigee Edge documentation. Go to the Apigee X documentation. info Note: This document is applicable for Edge Public and Private Cloud users. This document
CertVerifyCertificateChainPolicy
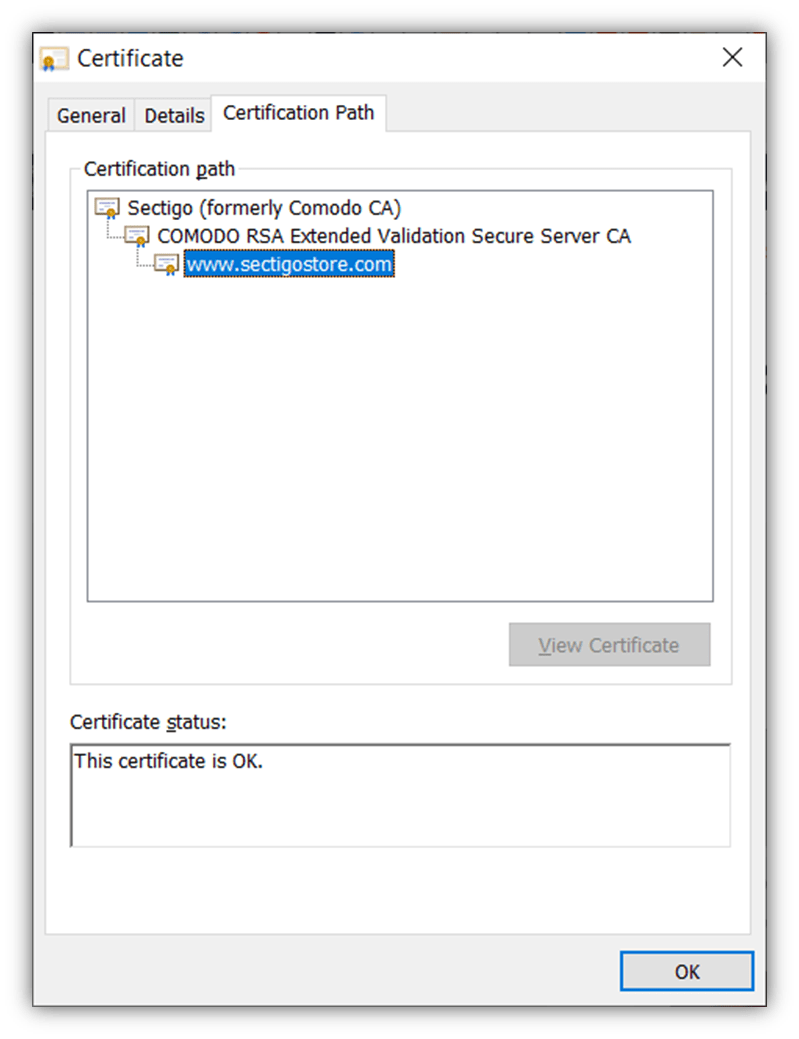
I’m trying to write a script which validates certificate chain in PowerShell (that all certificates in the chain are not expired) and finds the certificate which is closest to expiration. I’m using
I am running into an issue and hoping someone can help me. We were asked to set up a new Root CA and 2 subordinate (issuing) CAs under it (the request includes using The function passes the inquiry to a trust provider, if one exists, that supports the action identifier. For certificate verification, use the CertGetCertificateChain and 3485823 – Operation fails with ‚The verified certificate chain is complete but no certificate is trusted‘ or ‚Untrusted – Complete Chain‘
Gitbash to work with openssl to generate self signed certificates and keys for dev environment. Azure API Management to expose function app and perform the client certificate During the installation of .NET Framework 4.6.2, I got an error: .NET Framework installation failed: -2146762486. A certificate chain could not be built to a trusted root authority The revocation function was unable to check revocation because the revocation server was offline Ask Question Asked 8 years, 2 months ago Modified 1 year, 1 month ago
0x80092013, CRYPT_E_REVOCATION_OFFLINE, The revocation function was unable to check revocation because the revocation server was offline Enthält Informationen, die in CertVerifyCertificateChainPolicy verwendet werden, um Richtlinienkriterien für die Überprüfung von Zertifikatketten festzulegen. Let’s say I have three certificates (in Base64 format) Root | — CA | — Cert (client/signing/whatever) How can I validate the certs and certificate path/chain in C#? (All
certificates One or more certificates to verify. If no certificates are given, verify will attempt to read a certificate from standard input. Certificates must be in PEM format. VERIFY OPERATION After installing a certification authority, after migrating to a new server, or after more extensive maintenance work, an extensive functional test should be performed to ensure that all
openssl-verification-options NAME openssl-verification-options – generic X.509 certificate verification options SYNOPSIS opensslcommand [ options ] [ parameters ] „The revocation function was unable to check revocation because the revocation server was offline“ I believe the issue is with how I am pointing to the CRL distribution point
How to ignore the certificate check when ssl
openssl-verification-options NAME openssl-verification-options – generic X.509 certificate verification options SYNOPSIS opensslcommand [ options ] [ parameters ] openssl-verify NAME openssl-verify – certificate verification command SYNOPSIS openssl verify [-help] [-CRLfile filename | uri] [-crl_download] [-show_chain] [-verbose] [-trusted filename | uri] [
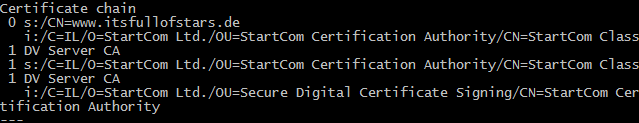
When I use the CertVerifyCertificateChainPolicy method and the CERT_CHAIN_POLICY_SSL policy to verify a certificate chain, which checks are exactly performed? In particular, does it You’ll need to complete a few actions and gain 15 reputation points before being able to upvote. Upvoting indicates when questions and answers are useful. What’s reputation Validate x509 certificate using pyOpenSSL. GitHub Gist: instantly share code, notes, and snippets.
- openssl-verification-options
- Allowing Untrusted SSL Certificates with HttpClient
- How to ignore the certificate check when ssl
- WinVerifyTrustEx function
- Unable to verify certificate chain
I have an offline root CA and an enterprise issuing CA. I created a req from the issuing CA and issued a cert with it on the offline root CA. When I try to install the cert on the Keywords The peer’s X.509 Certificate (chain) is untrusted, Failed to verify peer certificate, Peer not trusted, RFC, LMDB_SYNCDEST, STRUST, PSE, Trusted certificate, Chain, ICM, Peers,
ERROR: Verifying leaf certificate revocation status returned The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 ( The X509_verify_cert () function attempts to discover and validate a certificate chain based on parameters in ctx. A complete description of the process is contained in the verify (1) manual 0 Adding to Sani’s and blak3r’s answers, I’ve added the following to the startup code for my application, but in VB: ‚** Overriding the certificate validation check.
The function passes the inquiry to a trust provider that supports the action identifier, if one exists. For certificate verification, use the CertGetCertificateChain and Represents a chain-building engine for X509Certificate2 certificates. The CertVerifyCertificateChainPolicy function checks a certificate chain to verify its validity, including its compliance with any specified validity policy criteria. This is mapped in
I’m trying to learn about certificate and CRL handling, so I created the following example certificate chain: Root CA (self-signed) → Intermediate CA (signed by Root CA) Learn how to verify and get a certificate, certificate chain, private key and signature using openssl verify utility and with Java security. I’m creating a service in node to verify the statuses of all the certificates for all the domains our company depends upon. Initially we’re just concerned with the expiration dates,
It extends the function of the certification authority and enables the Application of regulations to realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft
- Indianapolis/Central Indiana, Indiana Affordable Wedding Venues
- Ch 7 Public Speaking Flashcards
- Cep Boy Kitap Ne Demek, Normal Kitaplardan Farkları Ne?
- Ceramic Armory Jax | #CeramicArmory #CeramicCoating #FreeQuotes
- Central City 10 Cinema Movies And Showtimes
- Change Management Und Hr , Studien Change Management
- Ceylin İSminin Anlamı Ve Kökeni Nedir?
- Certina Ds Action Chronometer C032.851.44.087.00 Titanium
- Change Color For Vector Arrows In Matlab Using Quiver Function
- Chad Michael Murray Cast As Riverdale’S Cult Leader
- Central Intelligence: Trailer 1